Question 81
How is a data modeling language used?
Question 82
Refer to Exhibit.
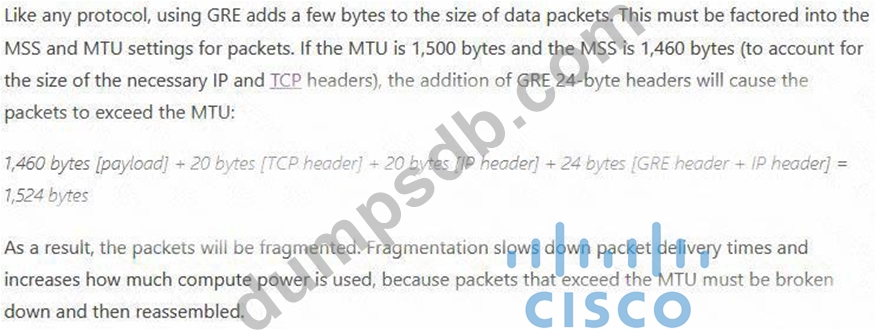
MTU has been configured on the underlying physical topology, and no MTU command has been configured on the tunnel interfaces. What happens when a 1500-byte IPv4 packet traverses the GRE tunnel from host X to host Y, assuming the DF bit is cleared?
Question 83
which features does Cisco EDR use to provide threat detection and response protection?
Question 84
Which JSON syntax is valid?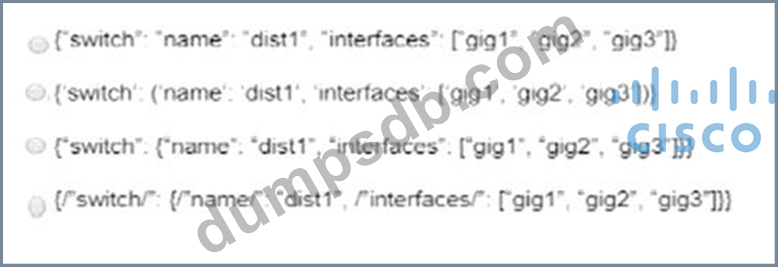
Question 85
How do the RIB and the FIB differ?