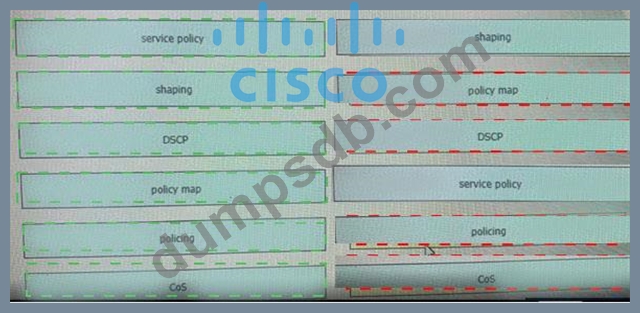
Question 376
Drag and drop the Qos mechanisms from the left to the correct descriptions on the right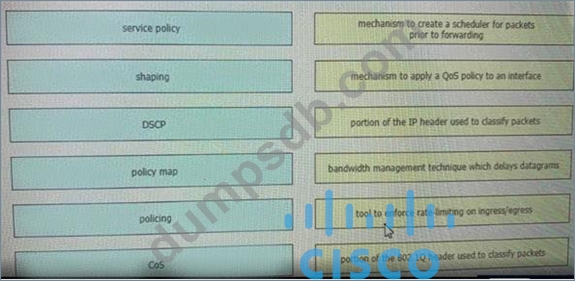
Question 377
Refer to the exhibit.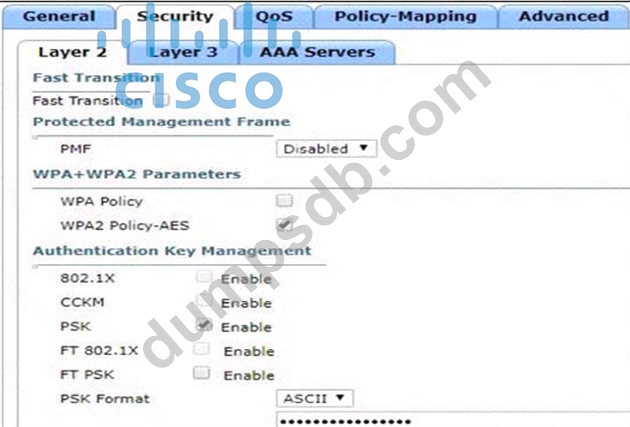
Based on the configuration in this WLAN security setting, Which method can a client use to authenticate to the network?
Question 378
Which feature Is used to propagate ARP broadcast, and link-local frames across a Cisco SD-Access fabric to address connectivity needs for silent hosts that require reception of traffic to start communicating?
Question 379
Refer to the exhibit.
An engineer attempts to create a configuration to allow the Blue VRF to leak into the global routing table, but the configuration does not function as expected. Which action resolves this issue?
Question 380
Refer to the exhibit.
A company requires that all wireless users authenticate using dynamic key generation. Which configuration must be applied?