Question 116
A company recently implemented a new cloud storage solution and installed the required synchronization client on all company devices. A few months later, a breach of sensitive data was discovered. Root cause analysis shows the data breach happened from a lost personal mobile device.
Which of the following controls can the organization implement to reduce the risk of similar breaches?
Question 117
A security engineer is analyzing an application during a security assessment to ensure it is configured to protect against common threats. Given the output below: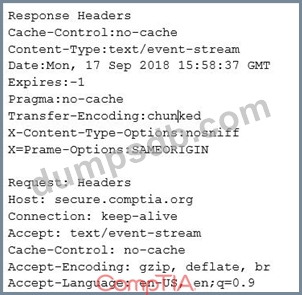
Which of the following tools did the security engineer MOST likely use to generate this output?
Question 118
The manager of the firewall team is getting complaints from various IT teams that firewall changes are causing issues.
Which of the following should the manager recommend to BEST address these issues?
Question 119
After a large organization has completed the acquisition of a smaller company, the smaller company must implement new host-based security controls to connect its employees' devices to the network. Given that the network requires 802.1X EAP-PEAP to identify and authenticate devices, which of the following should the security administrator do to integrate the new employees' devices into the network securely?
Question 120
An administrator has enabled salting for users' passwords on a UNIX box. A penetration tester must attempt to retrieve password hashes. Which of the following files must the penetration tester use to eventually obtain passwords on the system? (Select TWO).

