Question 246
A company monitors the performance of all web servers using WMI. A network administrator informs the security engineer that web servers hosting the company's client-facing portal are running slowly today. After some investigation, the security engineer notices a large number of attempts at enumerating host information via SNMP from multiple IP addresses.
Which of the following would be the BEST technique for the security engineer to employ in an attempt to prevent reconnaissance activity?
Question 247
Engineers at a company believe a certain type of data should be protected from competitors, but the data owner insists the information is not sensitive. An information security engineer is implementing controls to secure the corporate SAN. The controls require dividing data into four groups: non-sensitive, sensitive but accessible, sensitive but export-controlled, and extremely sensitive. Which of the following actions should the engineer take regarding the data?
Question 248
A security analyst is classifying data based on input from data owners and other stakeholders. The analyst has identified three data types:
1. Financially sensitive data
2. Project data
3. Sensitive project data
The analyst proposes that the data be protected in two major groups, with further access control separating the financially sensitive data from the sensitive project data. The normal project data will be stored in a separate, less secure location. Some stakeholders are concerned about the recommended approach and insist that commingling data from different sensitive projects would leave them vulnerable to industrial espionage.
Which of the following is the BEST course of action for the analyst to recommend?
Question 249
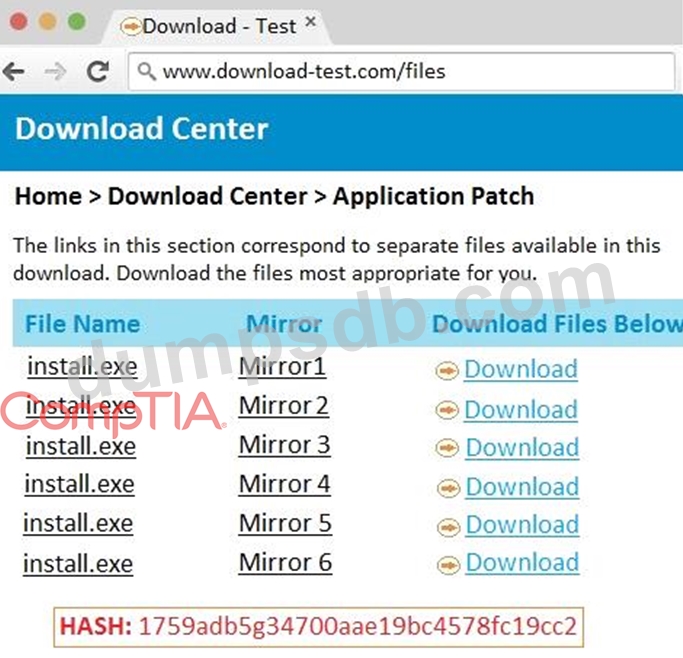
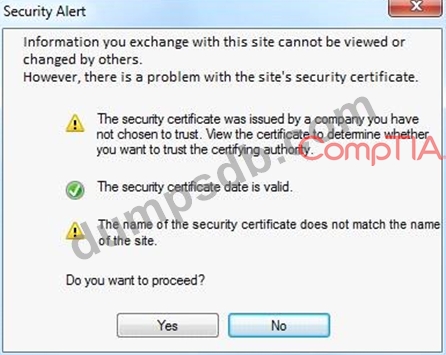
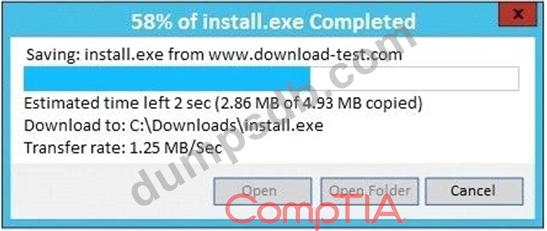
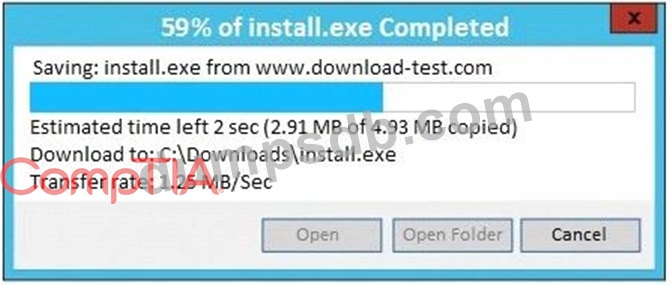
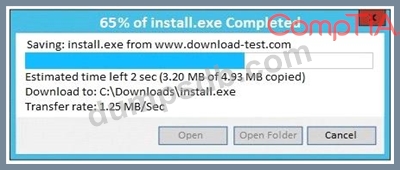
An administrator wants to install a patch to an application.
INSTRUCTIONS
Given the scenario, download, verify, and
install the patch in the most secure manner.
The last install that is completed will be the final submission.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Question 250
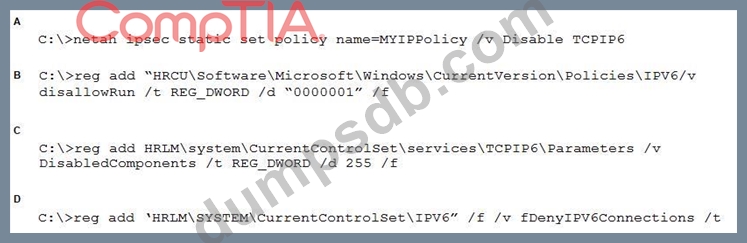
A security analyst, who is working in a Windows environment, has noticed a significant amount of IPv6 traffic originating from a client, even though IPv6 is not currently in use. The client is a stand-alone device, not connected to the AD that manages a series of SCADA devices used for manufacturing. Which of the following is the appropriate command to disable the client's IPv6 stack?