Question 6
A vulnerability scan has returned the following information:
Which of the following describes the meaning of these results?
Question 7
An analyst has noticed unusual activities in the SIEM to a .cn domain name. Which of the following should the analyst use to identify the content of the traffic?
Question 8
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS. If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean. If the vulnerability is valid, the analyst must remediate the finding. After reviewing the given information, select the STEP 2 tab in order to complete the simulation by selecting the correct "Validation Result" AND "Remediation Action" for each server listed using the drop down options.
Instructions:
If at any time you would like to bring back the initial state of the simulation, please select the Reset button.
When you have completed the simulation, please select the Done button to submit.
Once the simulation is submitted, please select the Next button to continue.





Question 9
A retail corporation with widely distributed store locations and IP space must meet PCI requirements relating to vulnerability scanning. The organization plans to outsource this function to a third party to reduce costs.
Which of the following should be used to communicate expectations related to the execution of scans?
Question 10
After completing a vulnerability scan, the following output was noted: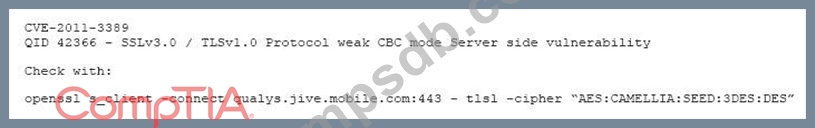
Which of the following vulnerabilities has been identified?

