Question 171
A corporation has implemented an 802.1X wireless network using self-signed certificates. Which of the following represents a risk to wireless users?
Question 172
A security analyst Is trying to capture network traffic In a web server that is suspected of using the DNS service for exfiltrating Information out of the network. The server usually transfers several gigabytes of data per day. and the analyst wants the size of the capture to be as reduced as possible. Which of the following commands should the analyst use to achieve such goals?
Question 173
A company invested ten percent of its entire annual budget in security technologies. The Chief Information
Officer (CIO) is convinced that, without this investment, the company will risk being the next victim of the
same cyber attack its competitor experienced three months ago. However, despite this investment, users
are sharing their usernames and passwords with their coworkers to get their jobs done. Which of the
following will eliminate the risk introduced by this practice?
Question 174
A security analyst wants to confirm a finding from a penetration test report on the internal web server. To do so, the analyst logs into the web server using SSH to send the request locally. The report provides a link to https://hrserver.internal/../../etc/passwd, and the server IP address is 10.10.10.15.
However, after several attempts, the analyst cannot get the file, despite attempting to get it using different ways, as shown below.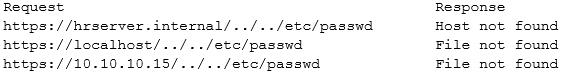
Which of the following would explain this problem? (Choose two.)
Question 175
A security analyst is assisting with a computer crime investigation and has been asked to secure a PC and deliver it to the forensic lab. Which of the following items would be MOST helpful to secure the PC? (Choose three.)

