Question 136
Which of the following router configuration modes changes terminal settings on a temporary basis, performs basic tests, and lists system information?
Question 137
Which of the following standards is an amendment to the original IEEE 802.11 and specifies security
mechanisms for wireless networks?
Question 138
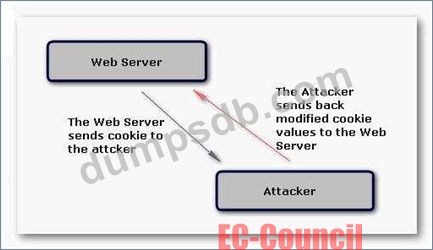
John visits an online shop that stores the IDs and prices of the items to buy in a cookie. After selecting the items that he wants to buy, the attacker changes the price of the item to 1.
Original cookie values:
ItemID1=2
ItemPrice1=900
ItemID2=1
ItemPrice2=200
Modified cookie values:
ItemID1=2
ItemPrice1=1
ItemID2=1
ItemPrice2=1
Now, he clicks the Buy button, and the prices are sent to the server that calculates the total price. Which of the following hacking techniques is John performing?
Question 139
What is needed for idle scan a closed port the next steps? Each correct answer represents a part of the solution. Choose all that apply.
Question 140
Token Ring is standardized by which of the following IEEE standards?