Question 116
What is a characteristic of an FC-AL implementation?
Question 117
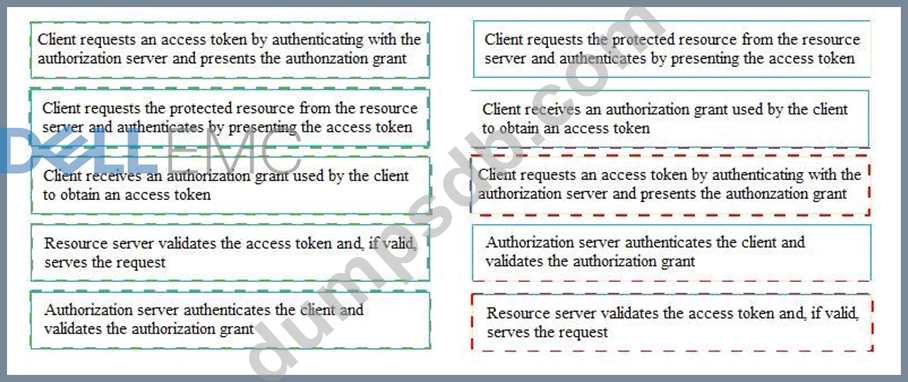
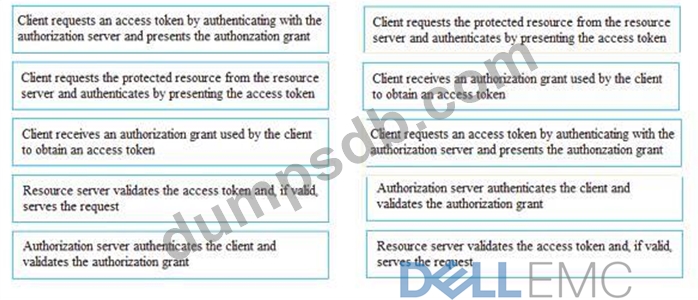
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?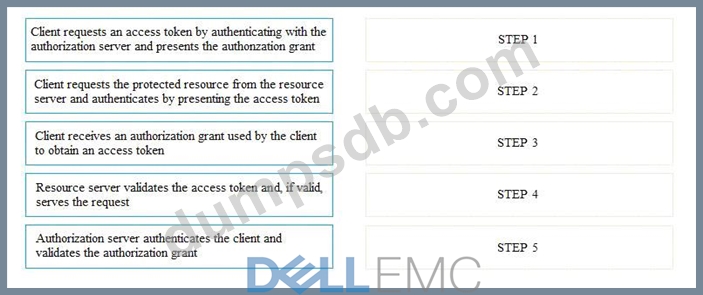
Question 118
Which technique is used in Kerberos to authenticate a client-server application across an insecure network?
Question 119
Which state change notifications (SCNs) are issued by an iSNS server to the registered devices?
Question 120
An organization plans to deploy a new application in their environment. The new application requires 4 TB of storage space. During peak workloads, the application is expected to generate
4900 IOPS with a typical I/O size of 8 KB. The capacity of each available disk drive is 500 GB.
The maximum number of IOPS a drive can perform at with a 70 percent utilization is 110 IOPS.
What is the minimum number of disk drives needed to meet the application's capacity and performance requirements given a RAID 0 configuration?