Question 61
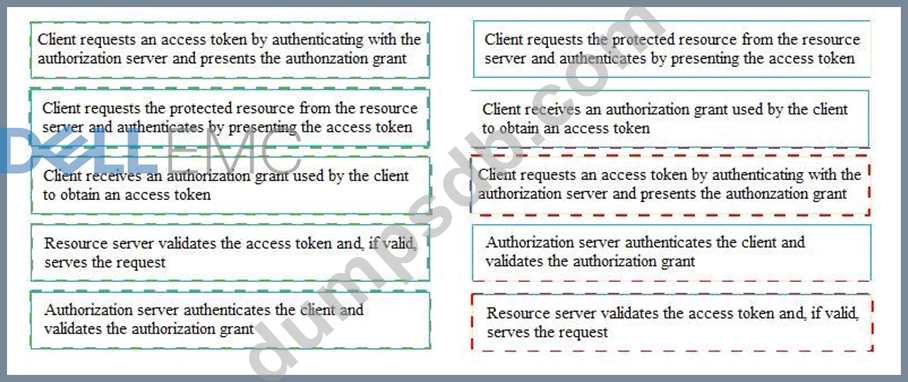
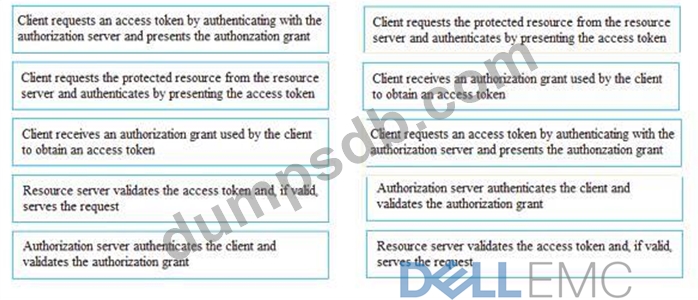
If the client requests authorization from the resource owner, what are the remaining sequence of steps to authenticate a user using OAuth control?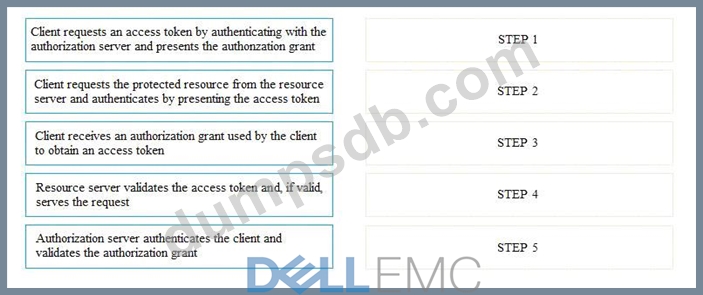
Question 62
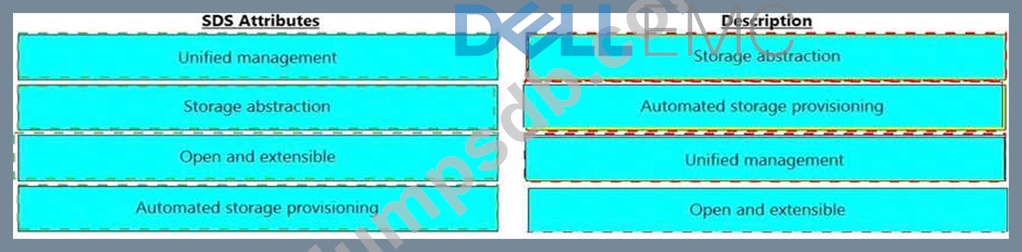
Match the software-defined storage (SDS) attributes with their respective description.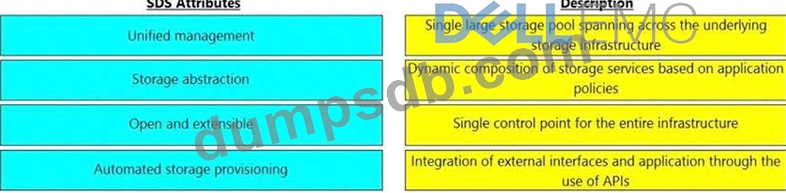
Question 63
Based on the exhibit, what does the "X" represent in the FCIP tunnel configuration?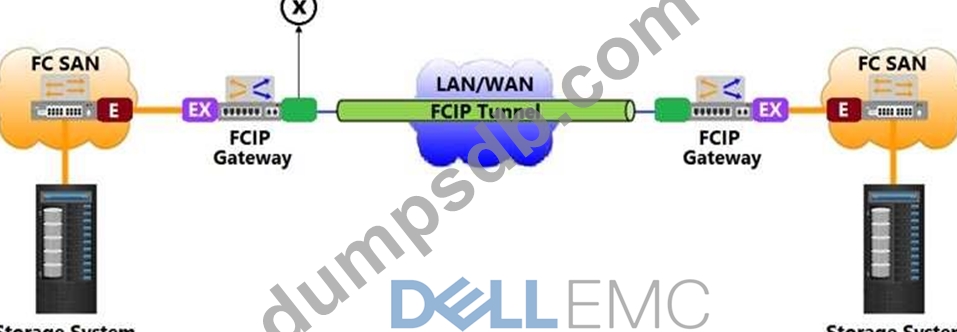
Question 64
Which method does an intrusion detection and prevention system (IDPS) use to identify intrusions by scanning and analyzing events to detect if they are statistically different from normal events?
Question 65
A system has three components and all three components need to be operational for 24 hours; Monday through Friday. During a particular week, failure of component 3 occurred as follows:
-Tuesday = 8 AM to 1 PM -Thursday = 5 PM to 10 PM -Friday = 5 AM to 10 AM What is the mean time between failures on component 3 for that week?