Question 21
Match each virtual network type with its characteristics.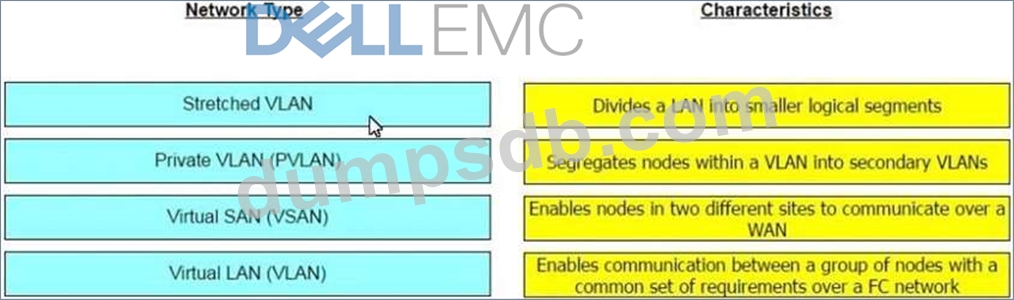
Question 22
In which technique does an application maintain limited functionality, even when some of the modules or supporting services of that application become unavailable?
Question 23

Which backup method type is represented in the exhibit?
Question 24
A compute system is configured to access files from a network-attached storage system. What is a characteristic of the file system?
Question 25
A specific intrusion detection and prevention system (IDPS) scans events against known attack patterns.
Which technique is the IDPS using?