Question 46
The HW network consists of Network A and B that are connected via Router HW1 and Router HW2. The HW network is shown in the following exhibit.
To set up an IPSec VPN between routers HW1 and HW2, which of the following crypto access-lists must be configured on Router HW1 in order to send LAN to LAN traffic across the encrypted VPN tunnel?
Question 47
One BD in VXLAN can correspond to multiple VNI.
Question 48
The HTTP protocol is based on TCP, so you can use the TCP Flood attack defense method to defend against HTTP Flood attacks.
Question 49
The topology diagram and configuration are as follows. Now hope that there are no detailed routing entries of 10.6.3.3/32 in the R1 routing table. Which of the following statements can achieve this requirement? (Multiple Choice)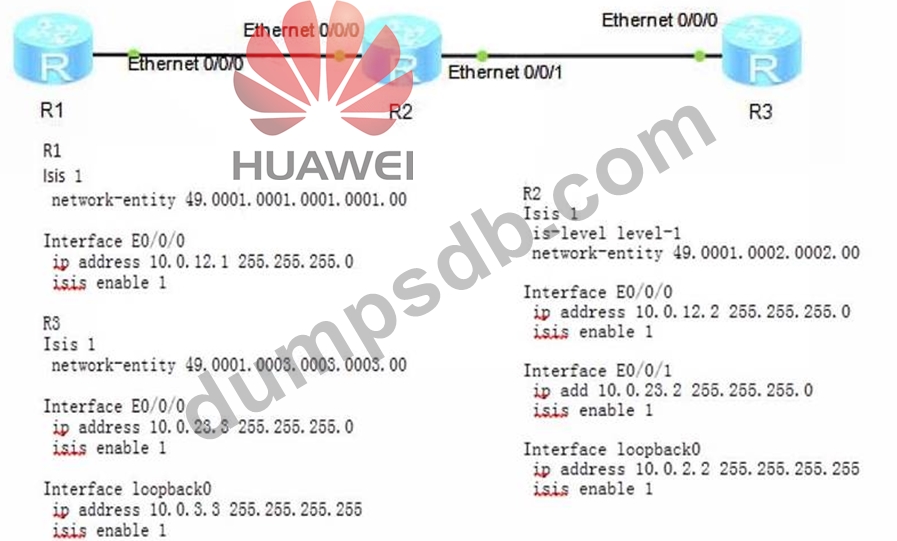
Question 50
The following statement about the security confederation SA in IPsec, which is wrong?

