Question 46
In the GRE configuration environment, which of the following interface or IP address is the local GRE device configuration of the end private network route required to point to? (Choose two.)
Question 47
As shown in the figure, a TCP connection is established between client A and server
B. Which of the following two "?" packet numbers should be?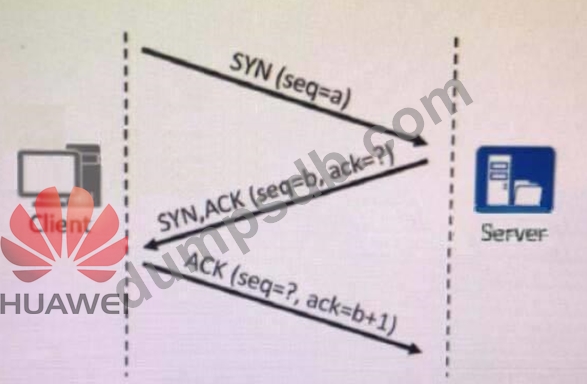
Question 48
The Protocol field in the IP header identifies the protocol used by the upper layer. Which of the following field values indicates that the upper layer protocol is UDP protocol?
Question 49
Which of the following description is correct about the sort of the call setup process for L2TP corridors?
1. L2TP tunnel
2. PPP connection
3. LNS authenticates users
4. Users accessintranet resources
5. Establish an L2TP session
Question 50
On the surface, threats such as viruses, vulnerabilities, and Trojans are the cause ofinformation security incidents, but at the root of it, information security incidents are also strongly related to people and information systems themselves.

