Question 51
Through display ike sa to see the result as follows, which statements are correct? (Multiple choice)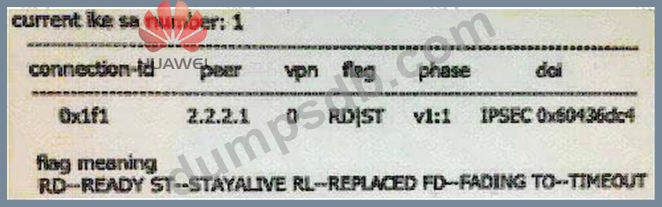
Question 52
Which of the following are in the certification area of ISO27001? (Multiple choice)
Question 53
Which of the following protocols can guarantee the confidentiality of data transmission? (Multiple Choice)
Question 54
Security policy conditions can be divided into multiple fields, such as source address, destination address, source port, destination port, etc. These fields are "and " , that is, only information in the message and all fields If you match, you can hit this strategy
Question 55
Which of the following is not the main form of computer crime?

