Question 61
According to the network diagram regarding hot standby, which of the following are correct? (Choose three answers)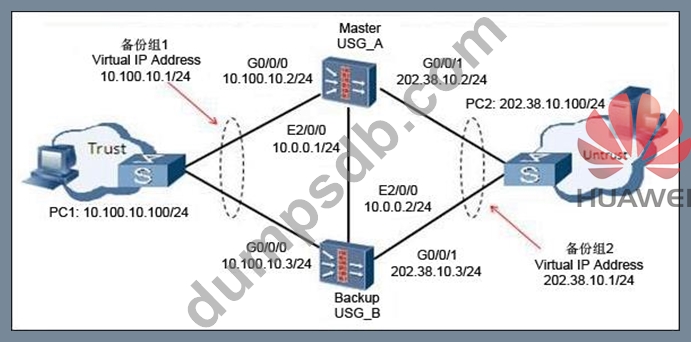
Question 62
HTTP Flood attacks refer indirectly to the target server to initiate a large number of HTTP packets to burden the server so that it can not respond to normal requests.
Through the interface rate limit function, HTTP flood attacks can be prevented.
Question 63
An attack source will spoof the server and send a large number of SYN-ACK packets to the attacking target network or server. If the destination port of the packet is the TCP service port of the attacked server, the TCP protocol stack of the server will be abnormal. What is it?
Question 64
In the IPsec NAT traversal application scenarios, the firewall must be configured to initiate party NAT traversal, and the other end can not configure firewall NAT traversal related commands.
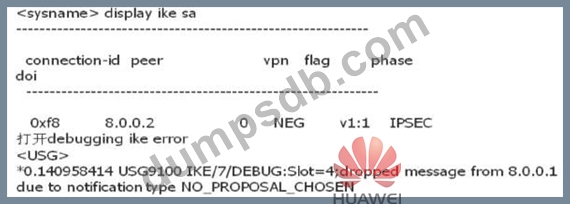
Question 65
An administrator can view the IPSec status information and debugging information as follows. What is the most likely fault?