Question 121
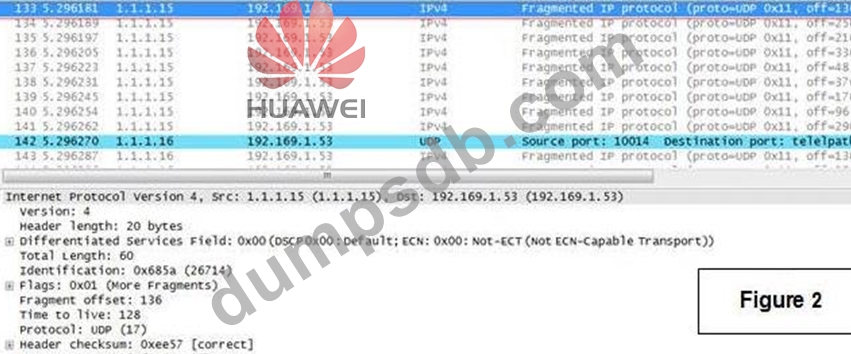
Figure 1 is the first to be attacked host. A packet capture screenshots is shown in line no
132, Figure 2 is a screenshot of attacked first host with line no. 133 packet capture.
Analyse what type of attack is this?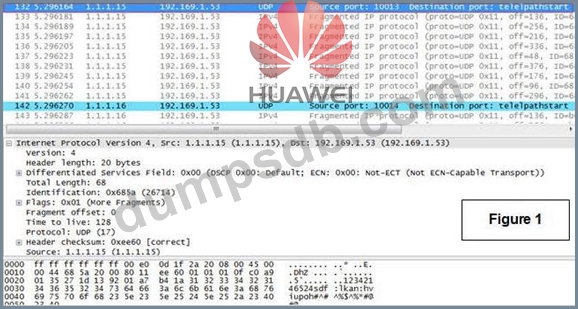
Question 122
With the Huawei Anti-DDoS equipment first packet discard technology, the defense is constantly changing the source IP address or source port number of attack packets.
Regarding the first packet discard technology, which of the following is not correct?
Question 123
For a virtual service technology, which of the following statements is correct?
Question 124
Which of the following is a drawback of an L2TP VPN?
Question 125
Which is incorrect about the IKE DPD statement?

