Question 116
To implement the dual-system hot standby function of the USG6000 firewall, which of the following protocols is not required?
Question 117
Regarding the Radius authentication process, refer to the following steps:
1. Network device Radius client (network access server) receives the user name and password, and sends an authentication request to the Radius server.
2. When a user logs into the USG access servers and other network devices, the user name and password will be sent to the network access server.
3. After the Radius server receives a valid request to complete the request and the required user authorization information is sent back to the client.
Which of the following is a correct sequence?
Question 118
Which of the statement is correct after going through the output of the command "display ike sa" which is shown below?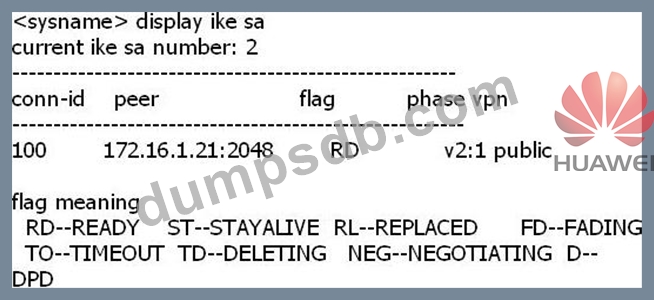
Question 119
Malformed packet attack techniques would use some legitimate data packets; these packets are of a legitimate application type.
Question 120
For IP-MAC address binding, packets with matching IP and MAC address will enter the next processing flow of the firewall. Packets that do not match IP and MAC address will be discarded.

