Question 156
DDos attacks work through the network to the target (usually a server, such as DNS server, WEB server) and sends a small amount of abnormal packets of non-traffic, so that the attacked server parses the message, causing the system to crash or become busy.
Question 157
When an attack occurs, many packets are found on the attacked host (1.1.129.32) as shown in the figure.
According to the analysis of the attack, what kind of attack is this attack?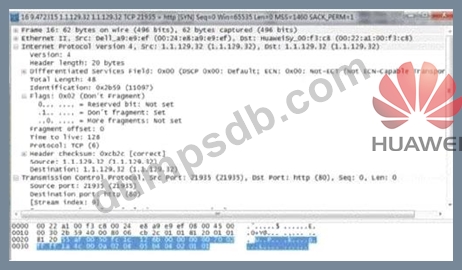
Question 158
When an IPSec VPN is set up on both ends of the firewall, the security ACL rules of both ends are mirrored.
Question 159
The Haiwei Secoway VPN client initiates an L2TP connection. The source port of the L2TP packet is 1710 and the port 1710 of the destination port.
Question 160
In a Firewall device through the source legality verification technology that defends SYN Flood attacks, the device receives a SYN packet, sending SYN-ASK probe packet and SYN packets to the source IP address of the host. If the host is real, which message will it send?

