Question 36
About L2TP over IPsec VPN, which of the following statements is correct? (Choose two answers)
Question 37
In Defense gate FIN / RST Flood attack method, conversation is checked. The workflow is that when the door FIN / RST packet rate exceeds the threshold; it discards packets, and then starts the conversation check.
Question 38
Two USG firewalls failed to establish an IPSec VPN tunnel through the NAT traversal mode. Run the display ike sa command to view the session without any UDP 500 session. What are the possible reasons?
Question 39
An enterprise networking is shown as the following figure, the hot standby is configured on USG_A and USG_B, and USG_A is the master device. The administrator wants to configure SSL VPN on the firewall so that branch office employees can access the headquarters through SSL VPN.
What should the SSL VPN virtual gateway address be?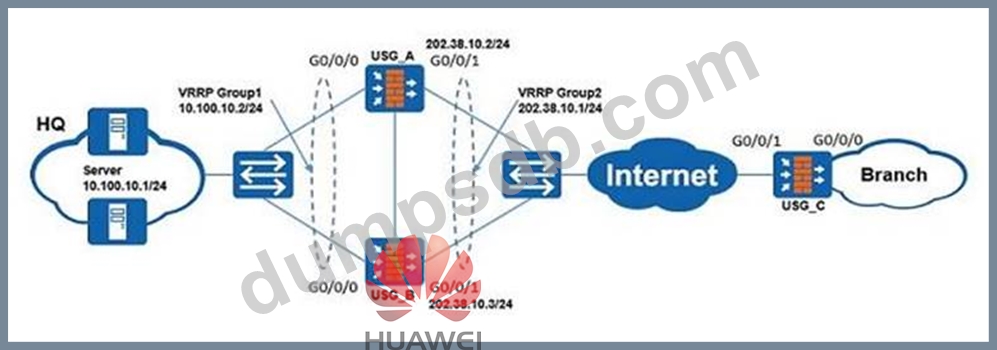
Question 40
Scenario: In the virtual firewall technology which is more commonly used in business to provide a phase out of business. If the virtual firewall VFW1 leased to companies A, virtual firewall VFW2 leased enterprise B, which of the following statement is not correct?

