Question 71
Regarding the sequence of file filtering technology processing flow, which of the following is correct?
(1) The security policy is applied as permit
(2) Protocol decoding
(3) File type recognition
(4) Application recognition
(5) File filtering
Question 72
Which of the following options does not belong to the characteristics of big data technology?
Question 73
The following figure is the diagram which shows the firewall and sandbox system linkage detection file.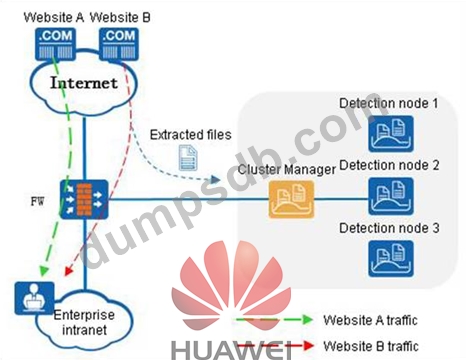
The Web Reputation feature is enabled on the firewall, and Site A is set as a trusted site and Site B is set as a suspicious site. Which of the following statements is correct?
Question 74
Regarding the description of keywords, which of the following is correct? (multiple choice)
Question 75
Which of the following is correct about worms and viruses?

