Question 31
Anomaly detection establishes the normal behavior characteristics of the system's main body through analysis of system audit data: In the detection, if the audit data in the system is different from the normal behavior characteristics of the established subject, it is considered an intrusion behavior. Which of the following can be used as the system body? (Multiple choices)
Question 32
Which of the following descriptions about viruses and Trojans are correct? (multiple choices)
Question 33
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?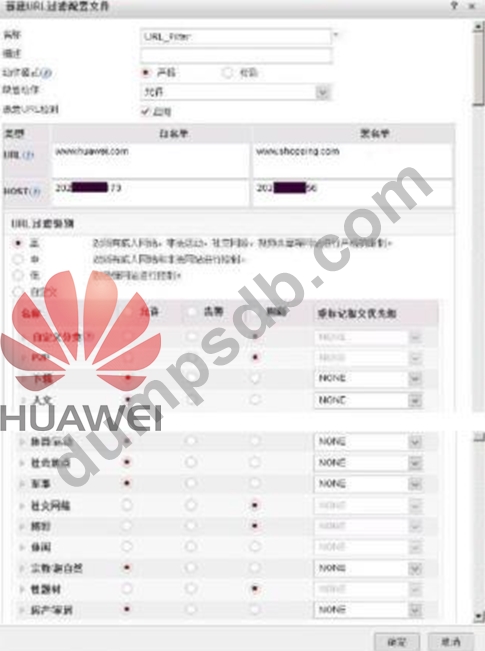
Question 34
Regarding the process of file filtering, which of the following statements is wrong?
Question 35
After the cleaning device establishes a BGP neighbor relationship with the peer router, uses BGP traffic diversion and policy routing reinjection, what configuration needs to be performed on the cleaning device? (Multiple Choice)

