Question 1
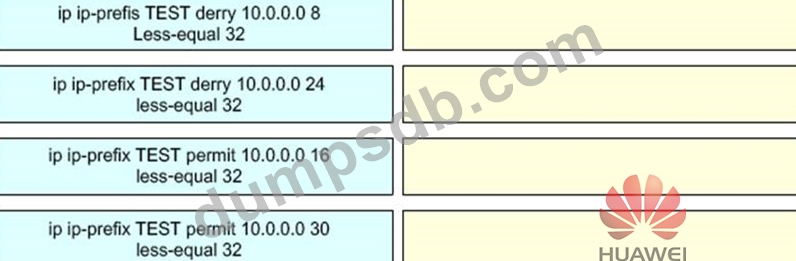
Network administrator A needs to permit or deny some specific routes, but administrator A is not proficient in configuration. Please help administrator A to sort the configurations reasonably so that the device can permit or deny specific routes as required in the figure.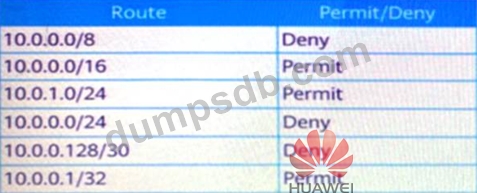
Question 2
Which of the following is not a hardware preparation for cutover?
Question 3
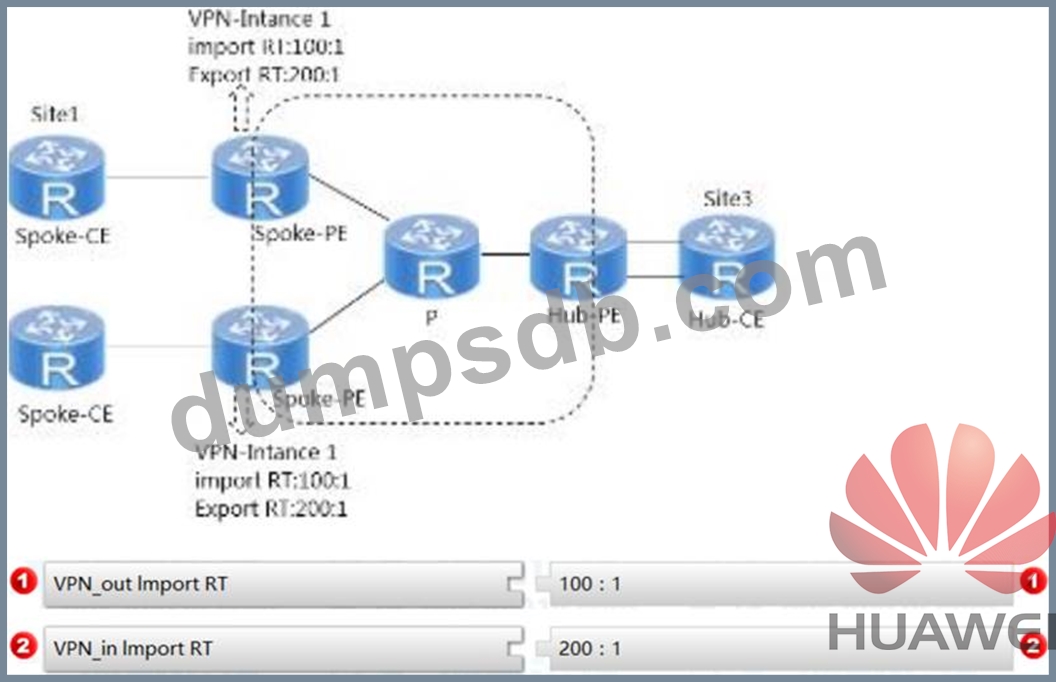
As shown in the figure, to enable the traffic between Site1 and Site2 to pass through the Hub-CE, VPN instances on two Spoke-PEs have been configured. Two VPN instances need to be created on the Hub-PE. The instance VPN in is used to receive routes from Spoke-PE, and the instance VPN out is used to advertise routes to Spoke-PE. Please select Import RT and Export RT for these two instances respectively. .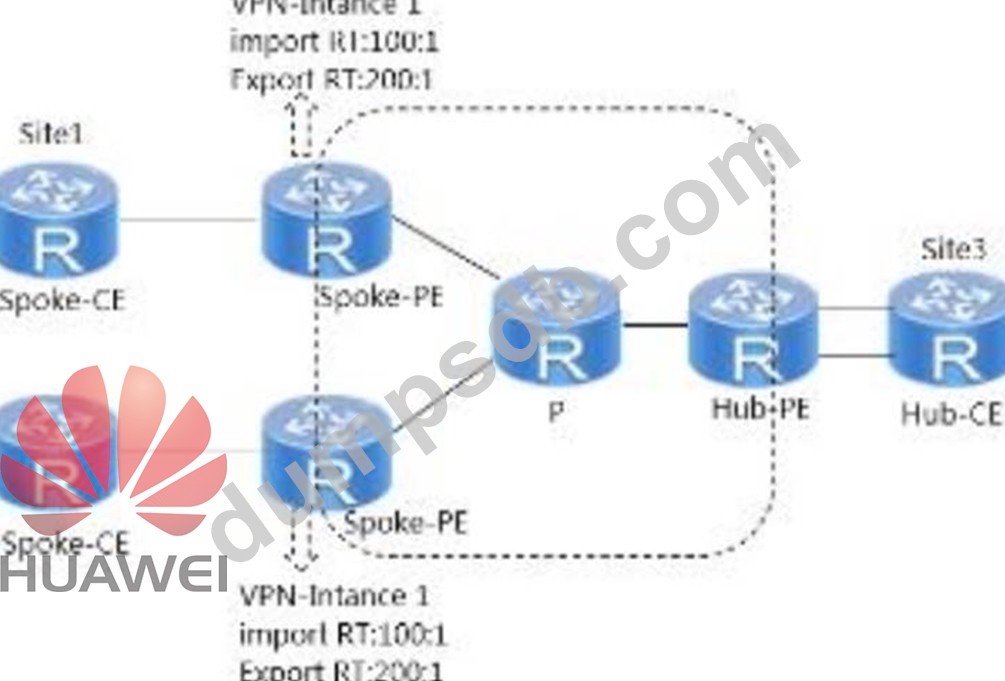
Question 4
Man-in-the-middle attacks or IP/MAC Spooping attacks can lead to information leakage and other hazards, and are more common in the intranet. To prevent man-in-the-middle attacks or IP/MAC Spooping attacks, which of the following configuration methods can be taken.
Question 5
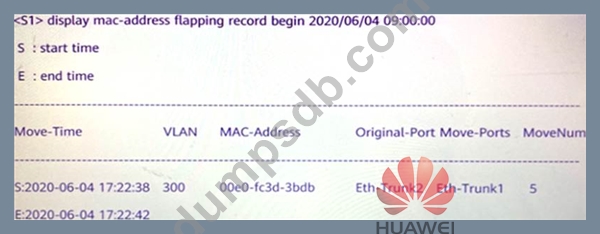
According to this figure, it can be known that in VLAN 300, on 2020-06-04, from 17:22:38 to 17:22:44, how many MAC flaps does the 00e0-fc3d-3bdb have?