Question 71
Users of a newly deployed VoIP solution report multiple instances of dropped or garbled calls. Thirty users connect to the primary site via a site-to-site VPN, and the primary site supplies a dial tone to all satellite locations. The network engineer who installed the equipment copied the configuration from a site that has two users on a low bandwidth DSL connection. Which of the following is MOST likely to restore telephone availability at the 30-user site?
Question 72
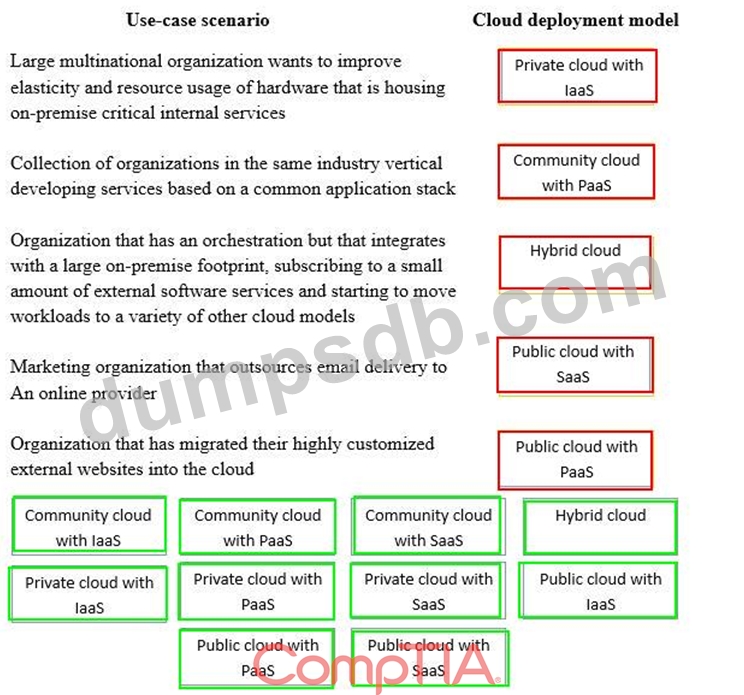
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.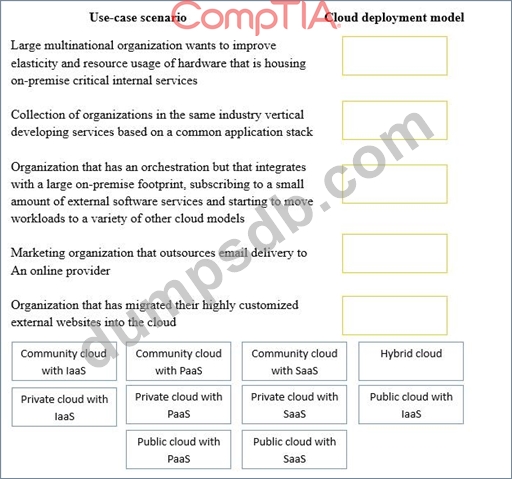
Question 73
A security manager needed to protect a high-security data center, so the manager installed a mantrap that can detect an employee's heartbeat, weight, and badge. Which of the following did the security manager implement?
Question 74
During a sprint, developers are responsible for ensuring the expected outcome of a change is thoroughly evaluated for any security impacts. Any impacts must be reported to the team lead.
Before changes are made to the source code, which of the following MUST be performed to provide the required information to the team lead?
Question 75
An information security manager is concerned that connectivity used to configure and troubleshoot critical network devices could be attacked. The manager has tasked a network security engineer with meeting the following requirements:
- Encrypt all traffic between the network engineer and critical
devices.
- Segregate the different networking planes as much as possible.
- Do not let access ports impact configuration tasks.
Which of the following would be the BEST recommendation for the network security engineer to present?