Question 76
A security engineer is helping the web developers assess a new corporate web application The application will be Internet facing so the engineer makes the following recommendation:
In an htaccess file or the site config add:
or add to the location block: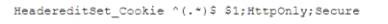
Which of the following is the security engineer trying to accomplish via cookies? (Select TWO)
Question 77
Given the following output from a local PC: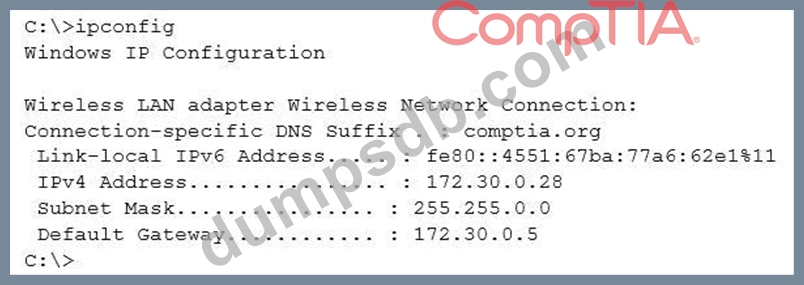
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
Question 78
A recent assessment identified that several users' mobile devices are running outdated versions of endpoint security software that do not meet the company's security policy. Which of the following should be performed to ensure the users can access the network and meet the company's security requirements?
Question 79
A security consultant is attempting to discover if the company is utilizing databases on client machines to store the customer data. The consultant reviews the following information: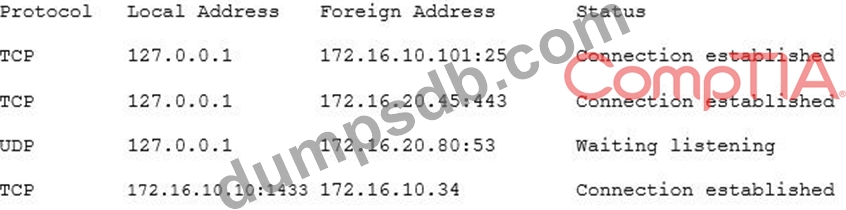
Which of the following commands would have provided this output?
Question 80
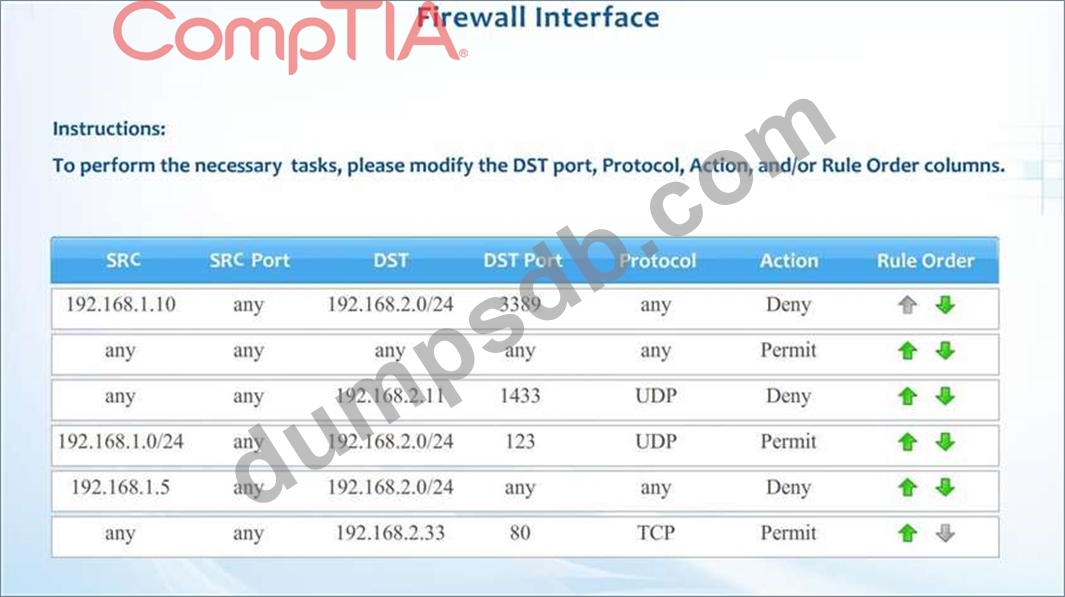
Lab Simulation
Compliance with company policy requires a quarterly review of firewall rules. A new administrator is asked to conduct this review on the internal firewall sitting between several Internal networks.
The intent of this firewall is to make traffic more restrictive. Given the following information answer the questions below:
User Subnet: 192.168.1.0/24
Server Subnet: 192.168.2.0/24
Finance Subnet:192.168.3.0/24
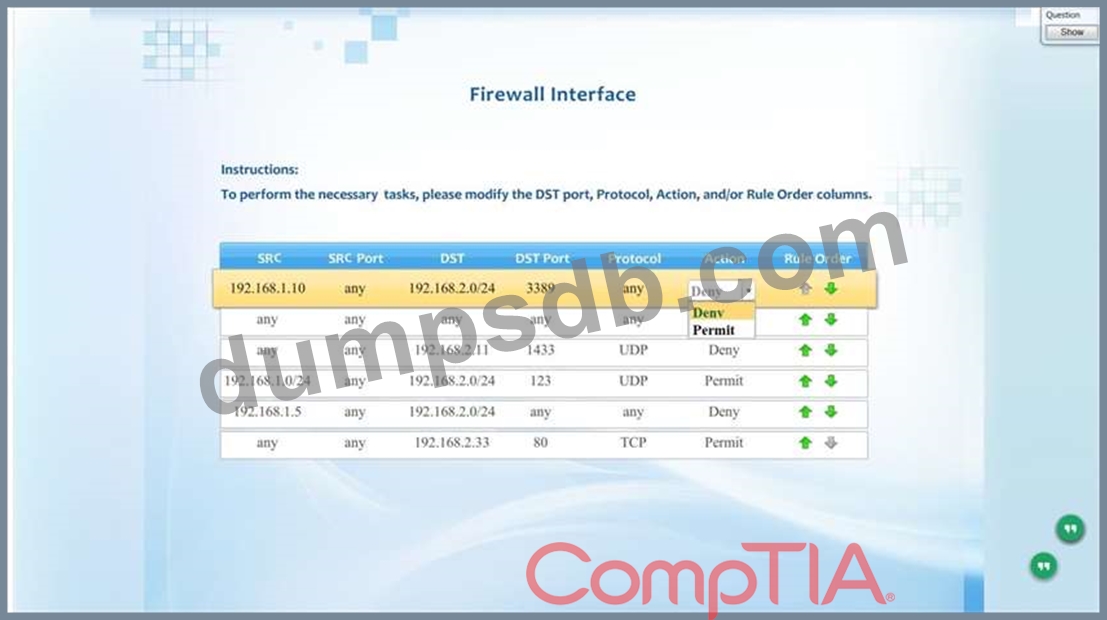
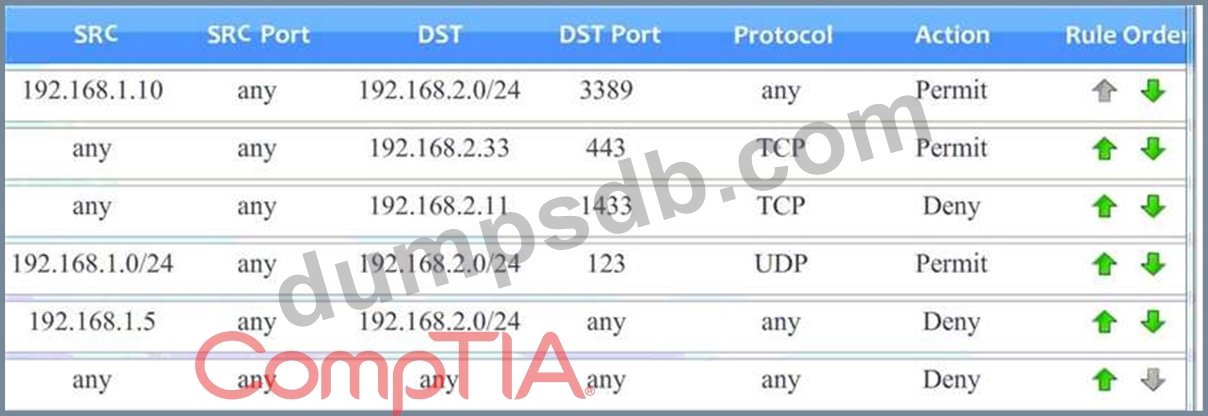
Instructions: To perform the necessary tasks, please modify the DST port, Protocol, Action, and/or Rule Order columns. Firewall ACLs are read from the top down Task 1) An administrator added a rule to allow their machine terminal server access to the server subnet. This rule is not working. Identify the rule and correct this issue.
Task 2) All web servers have been changed to communicate solely over SSL. Modify the appropriate rule to allow communications.
Task 3) An administrator added a rule to block access to the SQL server from anywhere on the network. This rule is not working. Identify and correct this issue.
Task 4) Other than allowing all hosts to do network time and SSL, modify a rule to ensure that no other traffic is allowed.