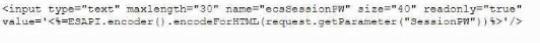Question 11
The following has been discovered in an internally developed application:
Error - Memory allocated but not freed:
char *myBuffer = malloc(BUFFER_SIZE);
if (myBuffer != NULL) {
*myBuffer = STRING_WELCOME_MESSAGE;
printf("Welcome to: %s\n", myBuffer);
}
exit(0);
Which of the following security assessment methods are likely to reveal this security weakness? (Select TWO).
Question 12
A financial consulting firm recently recovered from some damaging incidents that were associated with malware installed via rootkit. Post-incident analysis is ongoing, and the incident responders and systems administrators are working to determine a strategy to reduce the risk of recurrence. The firm's systems are running modern operating systems and feature UEFI and TPMs. Which of the following technical options would provide the MOST preventive value?
Question 13
A security engineer is investigating a compromise that occurred between two internal computers. The engineer has determined during the investigation that one computer infected another. While reviewing the IDS logs, the engineer can view the outbound callback traffic but sees no traffic between the two computers. Which of the following would BEST address the IDS visibility gap?
Question 14
A security technician is incorporating the following requirements in an RFP for a new SIEM:
New security notifications must be dynamically implemented by the SIEM engine The SIEM must be able to identify traffic baseline anomalies Anonymous attack data from all customers must augment attack detection and risk scoring Based on the above requirements, which of the following should the SIEM support? (Choose two.)
Question 15
A developer needs to provide feedback on a peer's work during the SDLC. While reviewing the code changes, the developers session ID tokens for a web application will be transmitted over an unsecure connection. Which of the following code snippets should the developer recommend implement to correct the vulnerability?
A)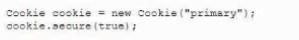
B)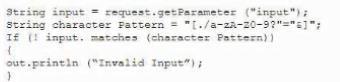
C)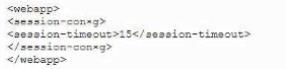
D)