Question 31
A company is not familiar with the risks associated with IPv6. The systems administrator wants to isolate IPv4 from IPv6 traffic between two different network segments. Which of the following should the company implement? (Choose two.)
Question 32
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.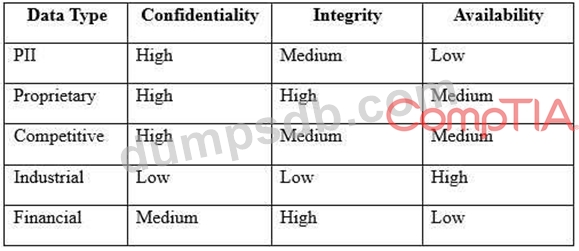
Based on the data classification table above, which of the following BEST describes the overall classification?
Question 33
A security incident responder discovers an attacker has gained access to a network and has overwritten
key system files with backdoor software. The server was reimaged and patched offline. Which of the
following tools should be implemented to detect similar attacks?
Question 34
A scrum master is working with a development team to develop new functionality of a mobile communication platform. As part of the SDLC. changes must be peer reviewed prior to inclusion in a build. To use the group's time as efficiently as possible. prior to which of the following phases must the scrum master ensure time for this activity is allocated'?
Question 35
A Chief Information Officer (CIO) publicly announces the implementation of a new financial system. As part of a security assessment that includes a social engineering task, which of the following tasks should be conducted to demonstrate the BEST means to gain information to use for a report on social vulnerability details about the financial system?

