Question 211
A security analyst has received the following requirements for the implementation of enterprise credential management software.
* The software must have traceability back to an individual
* Credentials must remain unknown to the vendor at all times
* There must be forced credential changes upon ID checkout
* Complexity requirements must be enforced.
* The software must be quickly and easily scalable with max mum availability Which of the following vendor configurations would BEST meet these requirements?
Question 212
An enterprise is trying to secure a specific web-based application by forcing the use of multifactor authentication. Currently, the enterprise cannot change the application's sign-in page to include an extra field. However, the web-based application supports SAML. Which of the following would BEST secure the application?
Question 213
The Information Security Officer (ISO) is reviewing a summary of the findings from the last COOP tabletop exercise. The Chief Information Officer (CIO) wants to determine which additional controls must be implemented to reduce the risk of an extended customer service outage due to the VoIP system being unavailable. Which of the following BEST describes the scenario presented and the document the ISO is reviewing?
Question 214
An engineer is evaluating the control profile to assign to a system containing PII, financial, and proprietary data.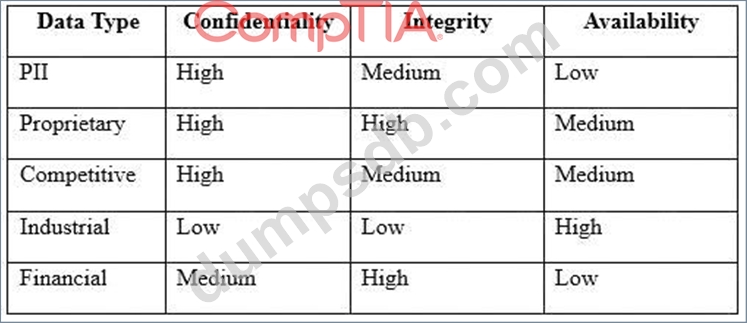
Based on the data classification table above, which of the following BEST describes the overall classification?
Question 215
The Chief Information Officer (CIO) is reviewing the IT centric BIA and RA documentation. The documentation shows that a single 24 hours downtime in a critical business function will cost the business $2.3 million. Additionally, the business unit which depends on the critical business function has determined that there is a high probability that a threat will materialize based on historical data. The CIO's budget does not allow for full system hardware replacement in case of a catastrophic failure, nor does it allow for the purchase of additional compensating controls.
Which of the following should the CIO recommend to the finance director to minimize financial loss?

