Question 216
Given the following code snippet: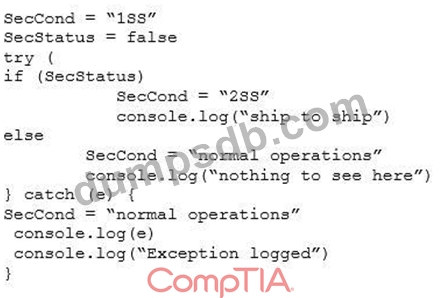
Which of the following failure modes would the code exhibit?
Question 217
An internal penetration tester was assessing a recruiting page for potential issues before it was pushed to the production website. The penetration tester discovers an issue that must be corrected before the page goes live. The web host administrator collects the log files below and gives them to the development team so improvements can be made to the security design of the website.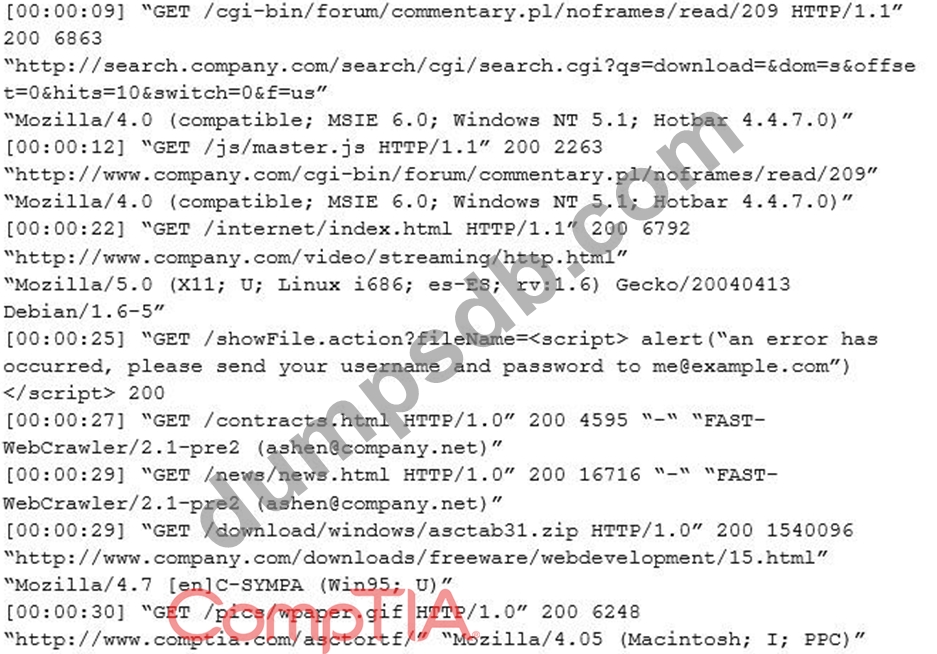
Which of the following types of attack vector did the penetration tester use?
Question 218
A Chief Information Securiy Officer (CISO) is reviewing technical documentation from various regional offices and notices some key differences between these groups. The CISO has not discovered any governance documentation. The CISO creates the following chart to visualize the differences among the networking used.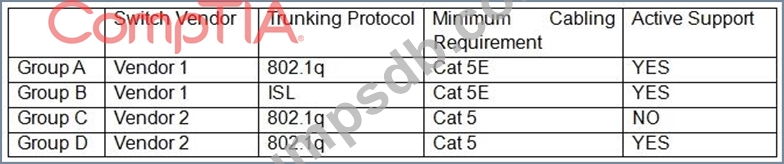
Which of the following would be the CISO's MOST immediate concern?
Question 219
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancements to the company's cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices.
Which of the following industry references is appropriate to accomplish this?
Question 220
Two competing companies experienced similar attacks on their networks from various threat actors. To improve response times, the companies wish to share some threat intelligence about the sources and methods of attack.
Which of the following business documents would be BEST to document this engagement?

