Question 346
A company has completed the implementation of technical and management controls as required by its adopted security, ponies and standards. The implementation took two years and consumed s the budget approved to security projects. The board has denied any further requests for additional budget. Which of the following should the company do to address the residual risk?
Question 347
A user asks a security practitioner for recommendations on securing a home network. The user recently
purchased a connected home assistant and multiple IoT devices in an effort to automate the home. Some
of the IoT devices are wearables, and other are installed in the user's automobiles. The current home
network is configured as a single flat network behind an ISP-supplied router. The router has a single IP
address, and the router performs NAT on incoming traffic to route it to individual devices.
Which of the following security controls would address the user's privacy concerns and provide the BEST
level of security for the home network?
Question 348
A company recently deployed an agent-based DLP solution to all laptop in the environment. The DLP solution is configured to restrict the following:
* USB ports
* FTP connections
* Access to cloud-based storage sites
* Outgoing email attachments
* Saving data on the local C: drive
Despite these restrictions, highly confidential data was from a secure fileshare in the research department.
Which of the following should the security team implement FIRST?
Question 349
Within the past six months, a company has experienced a series of attacks directed at various collaboration tools. Additionally, sensitive information was compromised during a recent security breach of a remote access session from an unsecure site. As a result, the company is requiring all collaboration tools to comply with the following:
* Secure messaging between internal users using digital signatures
* Secure sites for video-conferencing sessions
* Presence information for all office employees
* Restriction of certain types of messages to be allowed into the network.
Which of the following applications must be configured to meet the new requirements? (Choose two.)
Question 350
Providers at a healthcare system with many geographically dispersed clinics have been fined five times this year after an auditor received notice of the following SMS messages: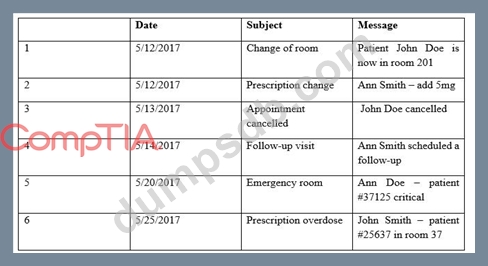
Which of the following represents the BEST solution for preventing future files?

