Question 326
A security analyst is reviewing the following pseudo-output snippet after running the command less
/tmp/file,tmp.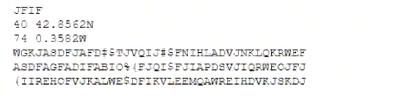
The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
Question 327
A security auditor suspects two employees of having devised a scheme to steal money from the company. While one employee submits purchase orders for personal items, the other employee approves these purchase orders. The auditor has contacted the human resources director with suggestions on how to detect such illegal activities. Which of the following should the human resource director implement to identify the employees involved in these activities and reduce the risk of this activity occurring in the future?
Question 328
An internal application has been developed to increase the efficiency of an operational process of a global manufacturer. New code was implemented to fix a security bug, but it has caused operations to halt. The executive team has decided fixing the security bug is less important than continuing operations.
Which of the following would BEST support immediate rollback of the failed fix? (Choose two.)
Question 329
A company's chief cybersecurity architect wants to configure mutual authentication to access an internal payroll website.
The architect has asked the administration team to determine the configuration that would provide the best defense against MITM attacks.
Which of the following implementation approaches would BEST support the architect's goals?
Question 330
An organization is selecting a SaaS provider to replace its legacy, in house Customer Resource Management (CRM) application. Which of the following ensures the organization mitigates the risk of managing separate user credentials?

