Question 301
Which of the following represents important technical controls for securing a SAN storage infrastructure? (Select TWO).
Question 302
The audit team was only provided the physical and logical addresses of the network without any type of access credentials.
Which of the following methods should the audit team use to gain initial access during the security assessment? (Choose two.)
Question 303
Click on the exhibit buttons to view the four messages.
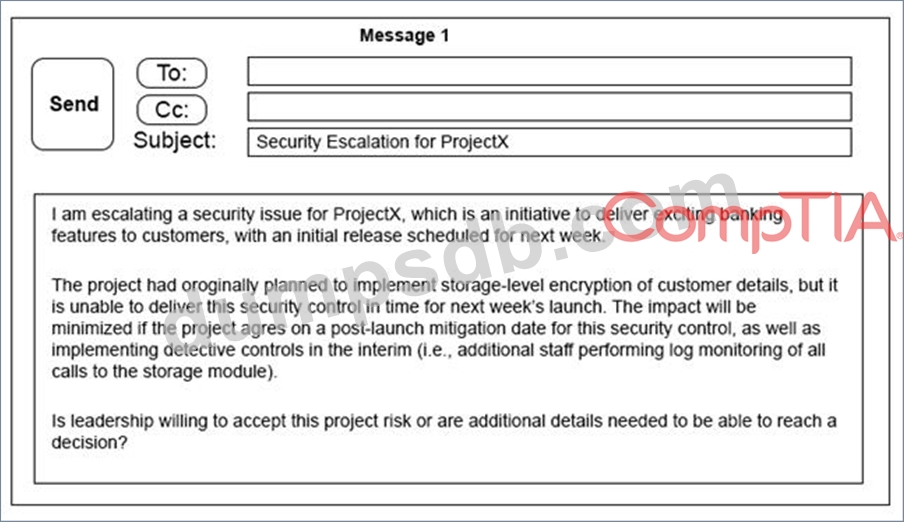
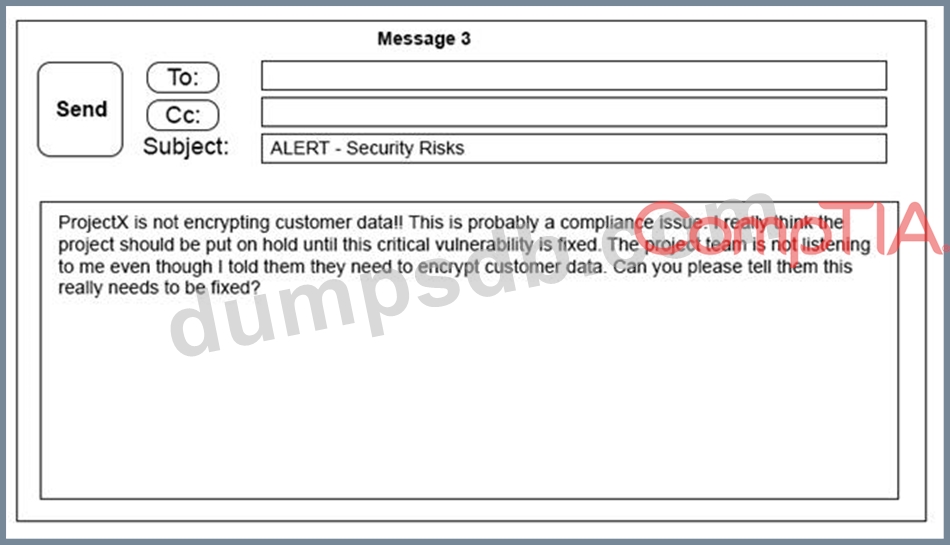
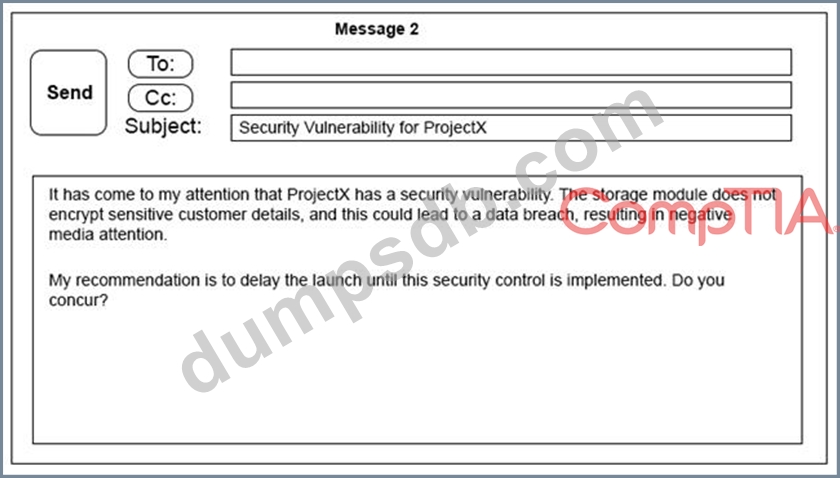
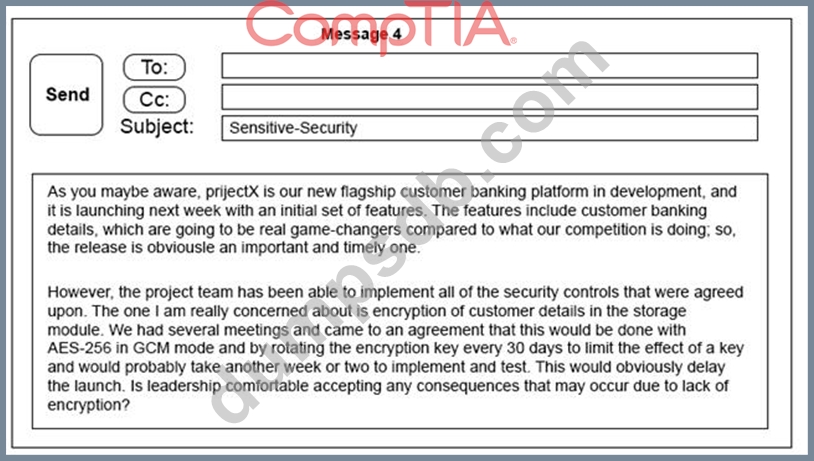
A security architect is working with a project team to deliver an important service that stores and processes
customer banking details. The project, internally known as ProjectX, is due to launch its first set of features
publicly within a week, but the team has not been able to implement encryption-at-rest of the customer
records. The security architect is drafting an escalation email to senior leadership.
Which of the following BEST conveys the business impact for senior leadership?
Question 304
The SOC has noticed an unusual volume of traffic coming from an open WiFi guest network that appears correlated with a broader network slowdown The network team is unavailable to capture traffic but logs from network services are available
* No users have authenticated recently through the guest network's captive portal
* DDoS mitigation systems are not alerting
* DNS resolver logs show some very long domain names
Which of the following is the BEST step for a security analyst to take next?
Question 305
Given the following: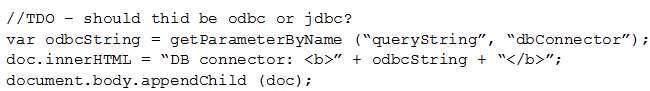
Which of the following vulnerabilities is present in the above code snippet?

