Question 291
A system owner has requested support from data owners to evaluate options for the disposal of equipment containing sensitive data. Regulatory requirements state the data must be rendered unrecoverable via logical means or physically destroyed. Which of the following factors is the regulation intended to address?
Question 292
The Chief Information Officer (CIO) wants to increase security and accessibility among the organization's cloud SaaS applications. The applications are configured to use passwords, and two-factor authentication is not provided natively.
Which of the following would BEST address the CIO's concerns?
Question 293
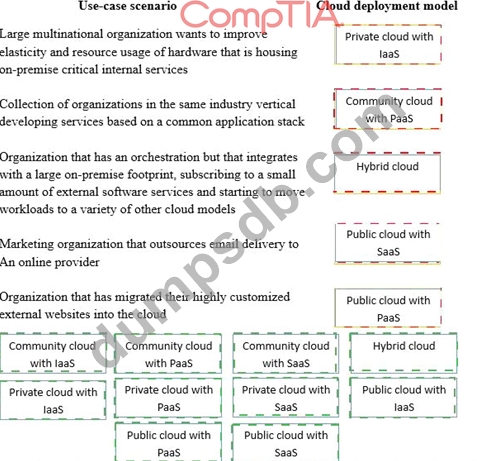
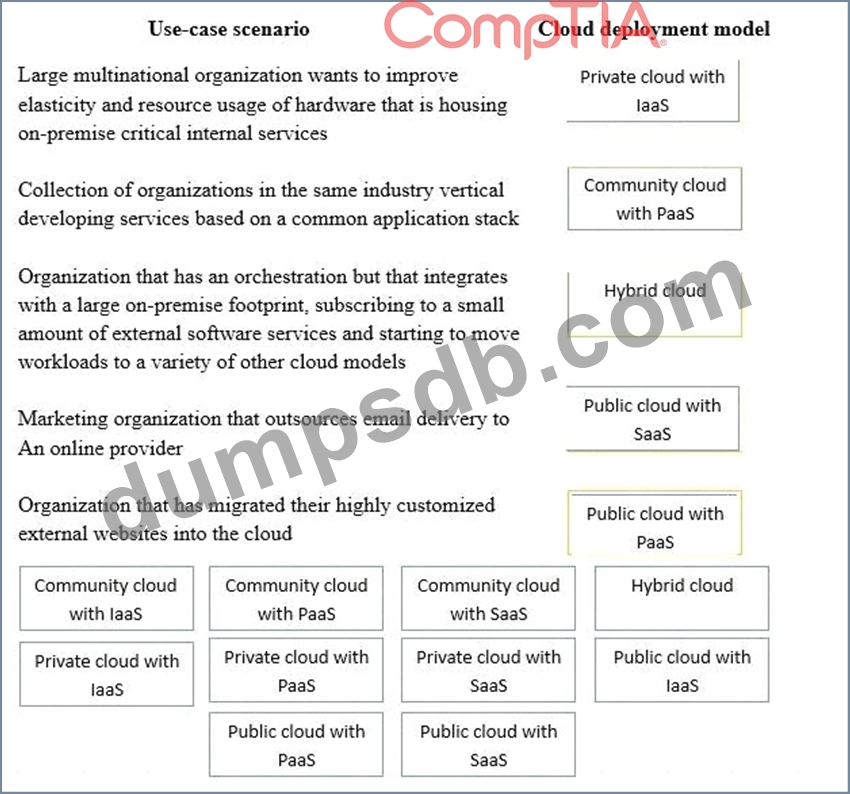
Drag and drop the cloud deployment model to the associated use-case scenario. Options may be used only once or not at all.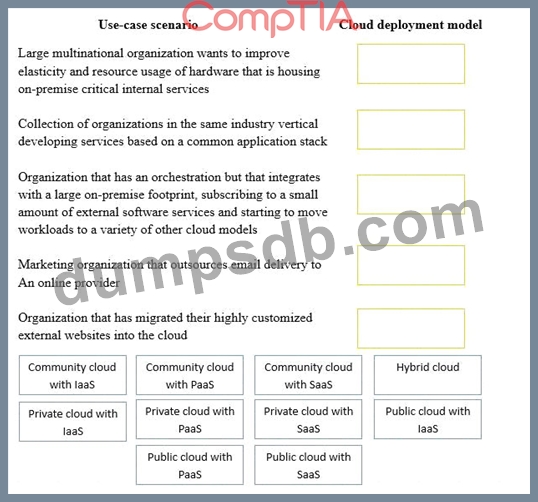
Question 294
At a meeting, the systems administrator states the security controls a company wishes to implement seem excessive, since all of the information on the company's web servers can be obtained publicly and is not proprietary in any way. The next day the company's website is defaced as part of an SQL injection attack, and the company receives press inquiries about the message the attackers displayed on the website.
Which of the following is the FIRST action the company should take?
Question 295
A large international business has completed the acquisition of a small business and it is now in the process of integrating the small business' IT department.
Both parties have agreed that the large business will retain 95% of the smaller business' IT staff.
Additionally, the larger business has a strong interest in specific processes that the smaller business has in place to handle its regional interests.
Which of the following IT security related objectives should the small business' IT staff consider reviewing during the integration process? (Select TWO).