Question 296
Given the following output from a local PC: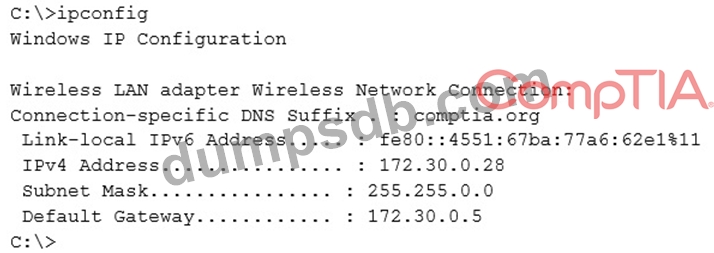
Which of the following ACLs on a stateful host-based firewall would allow the PC to serve an intranet website?
Question 297
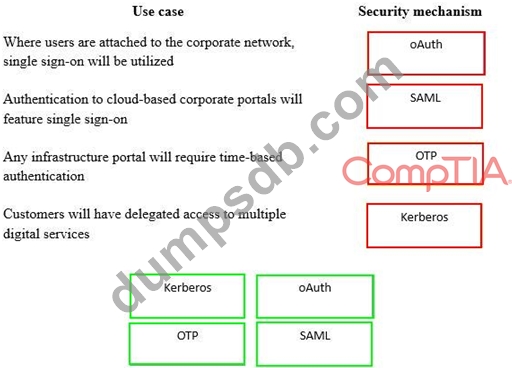
A security consultant is considering authentication options for a financial institution. The following authentication options are available. Drag and drop the security mechanism to the appropriate use case. Options may be used once.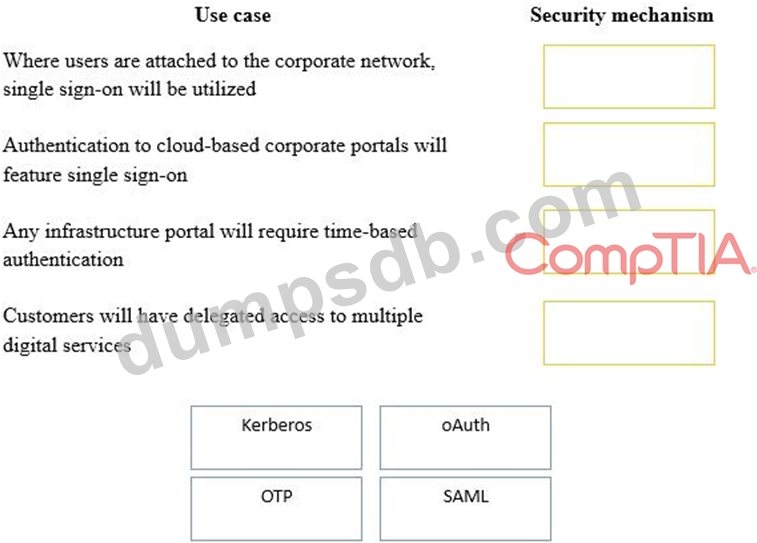
Question 298
While conducting a BIA for a proposed acquisition, the IT integration team found that both companies outsource CRM services to competing and incompatible third-party cloud services. The decision has been made to bring the CRM service in-house, and the IT team has chosen a future solution. With which of the following should the Chief Information Security Officer (CISO) be MOST concerned? (Choose two.)
Question 299
Providers at a healthcare system with many geographically dispersed clinics have been fined five times
this year after an auditor received notice of the following SMS messages: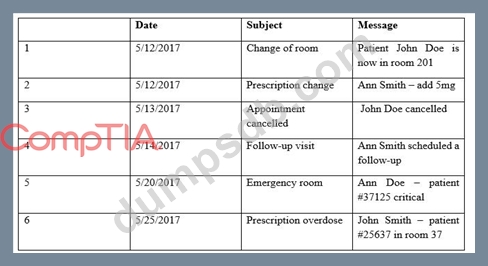
Which of the following represents the BEST solution for preventing future fines?
Question 300
A completely new class of web-based vulnerabilities has been discovered. Claims have been made that all common web-based development frameworks are susceptible to attack. Proof-of-concept details have emerged on the Internet. A security advisor within a company has been asked to provide recommendations on how to respond quickly to these vulnerabilities. Which of the following BEST describes how the security advisor should respond?