Question 276
The code snippet below controls all electronic door locks to a secure facility in which the doors should only fail open in an emergency. In the code, "criticalValue" indicates if an emergency is underway: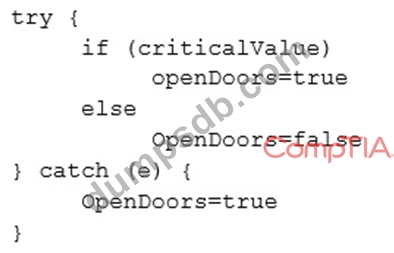
Which of the following is the BEST course of action for a security analyst to recommend to the software developer?
Question 277
A security administrator has noticed that an increased number of employees' workstations are becoming infected with malware. The company deploys an enterprise antivirus system as well as a web content filter, which blocks access to malicious web sites where malware files can be downloaded. Additionally, the company implements technical measures to disable external storage. Which of the following is a technical control that the security administrator should implement next to reduce malware infection?
Question 278
The Chief Executive Officer (CEO) of a company that allows telecommuting has challenged the Chief Security Officer's (CSO) request to harden the corporate network's perimeter. The CEO argues that the company cannot protect its employees at home, so the risk at work is no different. Which of the following BEST explains why this company should proceed with protecting its corporate network boundary?
Question 279
An infrastructure team is at the end of a procurement process and has selected a vendor. As part of the final negotiation, there are a number of outstanding issues, including:
1. Indemnity clauses have identified the maximum liability.
2. The data will be hosted and managed outside of the company's geographical location.
The number of users accessing the system will be small, and no sensitive data will be hosted in the solution.
As the security consultant of the project, which of the following should the project's security consultant recommend as the NEXT step?
Question 280
A systems administrator receives an advisory email that a recently discovered exploit is being used in another country and the financial institutions have ceased operations while they find a way to respond to the attack. Which of the following BEST describes where the administrator should look to find information on the attack to determine if a response must be prepared for the systems? (Choose two.)

