Question 51
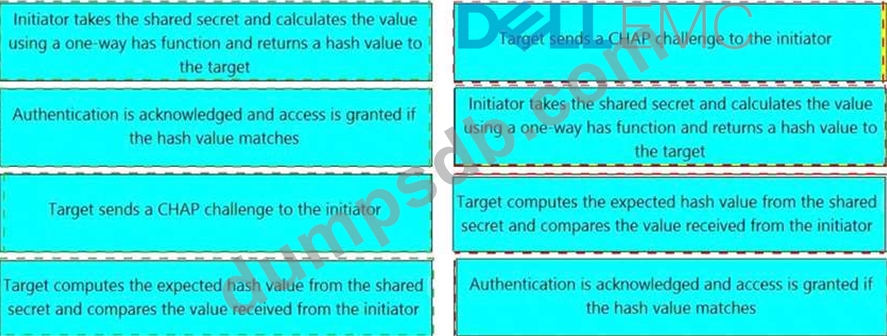
What is the correct sequence of steps to authenticate an initiator and a target using one-way Challenge Handshake Authentication Protocol (CHAP) after the initiator performs a login to the target?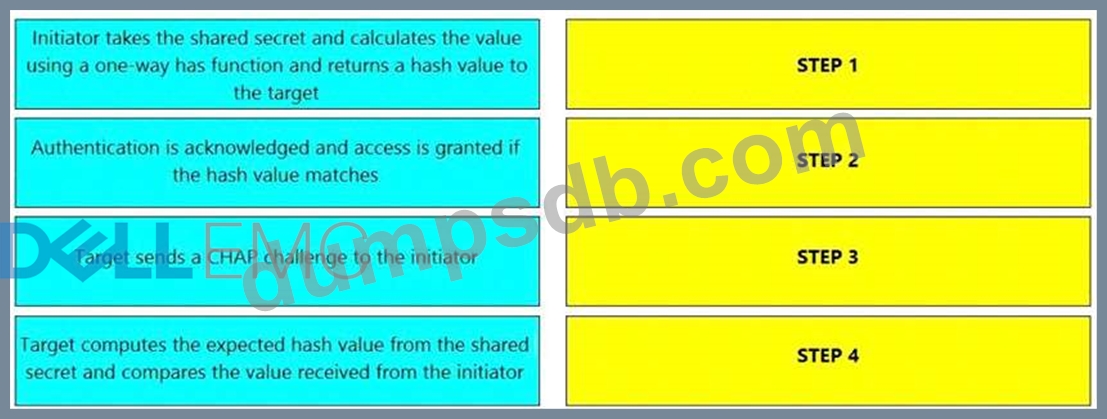
Question 52
What is an impact of a Denial-of-Service attack?
Question 53
When using a bridged iSCSI connection, which components facilitate communication between gateways?
Question 54
Which Dell EMC product is a disk-based backup and recovery solution that provides inherent source-based deduplication?
Question 55
Which Dell EMC product enables continuous protection for any PIT recovery and offers multi-site support?