Question 31
What accurately describes an attack vector in an IT infrastructure?
Question 32
What is a key advantage of implementing FCIP?
Question 33
What accurately describes an Incident in a storage infrastructure?
Question 34
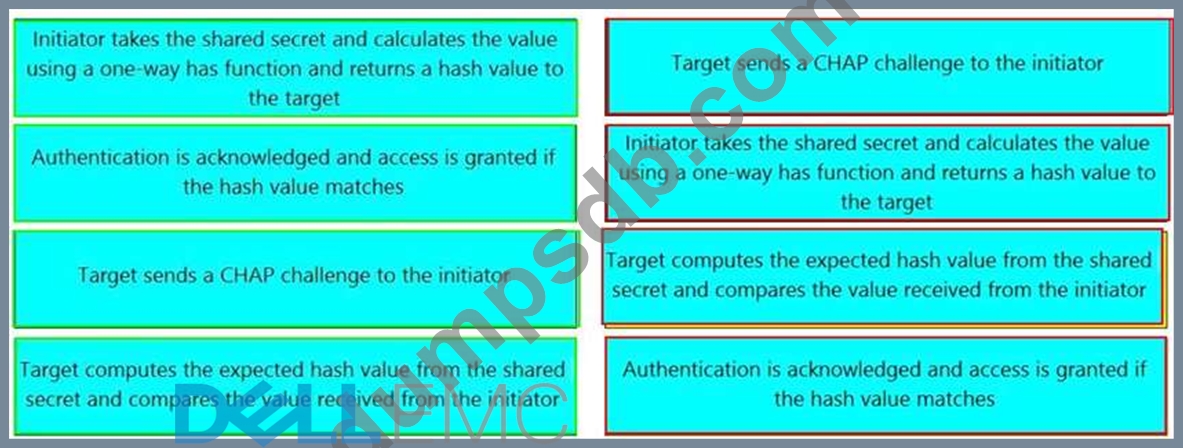
What is the correct sequence of steps to authenticate an initiator and a target using one-way Challenge Handshake Authentication Protocol (CHAP) after the initiator performs a login to the target?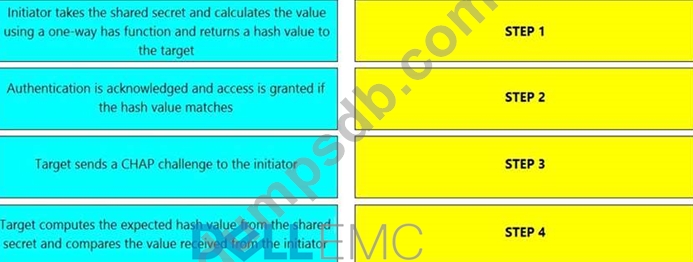
Question 35
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows:
* Monday = 10 AM to 12 PM
* Wednesday = 4 PM to 9 PM
* Thursday = 4 PM to 7 PM
* Friday = 3 PM to 6 PM
* Saturday = 9 AM to 1 PM
What is the availability of Port 2 in that week?