Question 36
What refers to the logging of all transactions when assessing the effectiveness of security controls in a cloud computing environment?
Question 37
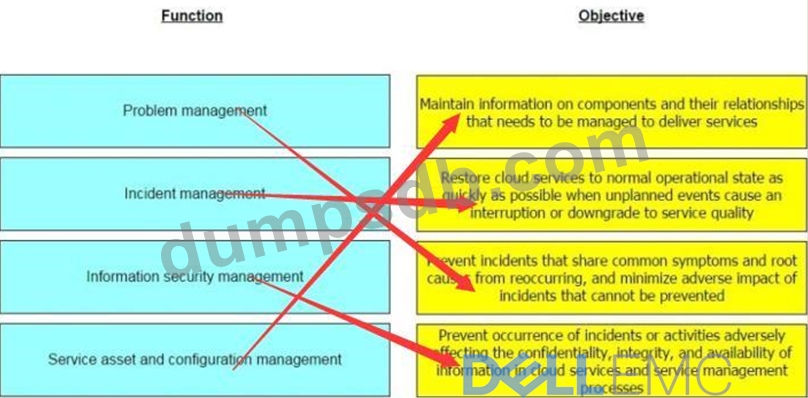
Match each key functions of service operation management with its objective.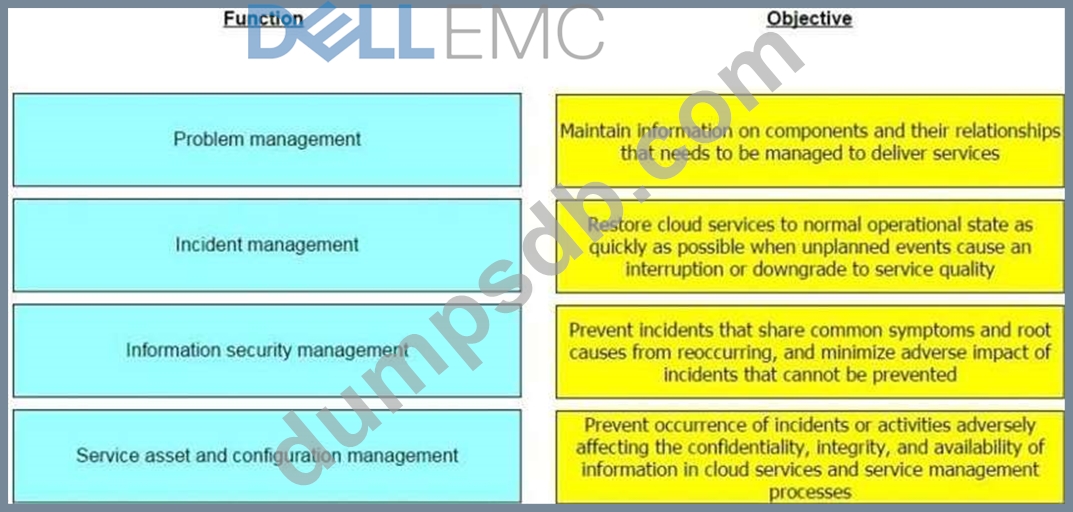
Question 38
Which method compares observed events with normal activities to identify abnormal patterns in a system?
Question 39
Which activity is conducted during the service termination phase of the cloud service lifecycle?
Question 40
What is a common characteristic of organizations that have adopted modern applications to unlock digital business advantage?