Question 16
Which principle is being followed when an analyst gathers information relevant to a security incident to determine the appropriate course of action?
Question 17
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
Question 18
Refer to the exhibit.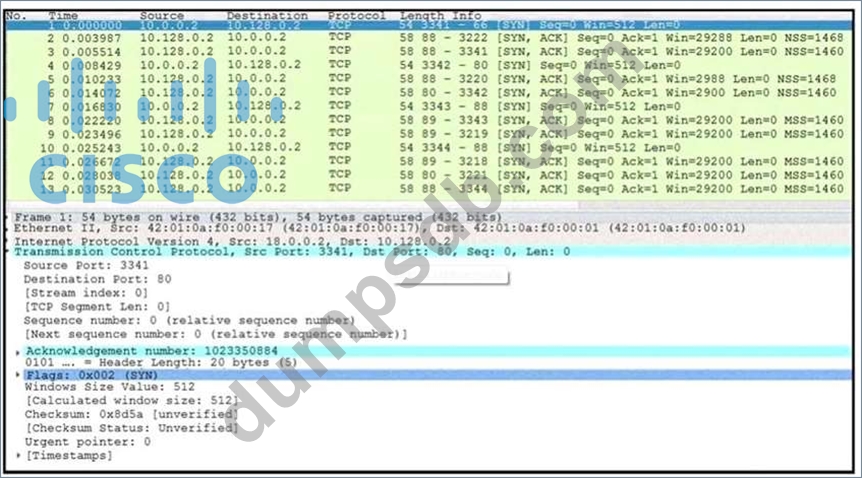
What is occurring in this network traffic?
Question 19
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
Question 20
Refer to the exhibit.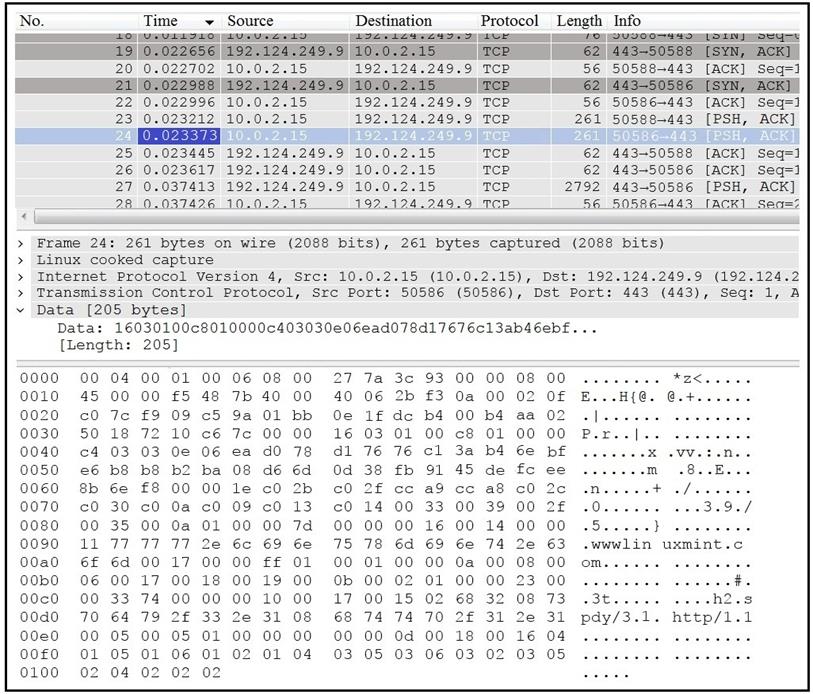
Which application protocol is in this PCAP file?

