Question 26
What is an attack surface as compared to a vulnerability?
Question 27
Drag and drop the data source from the left onto the data type on the right.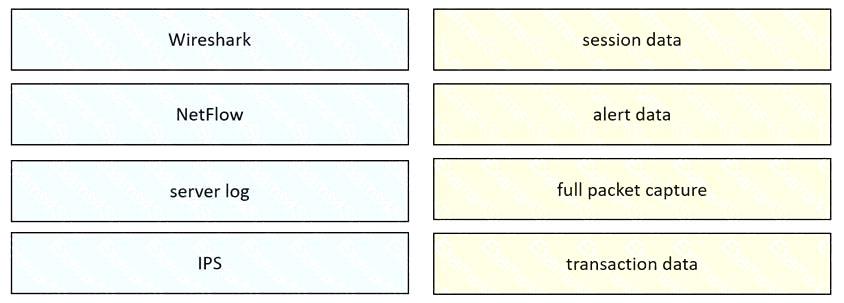
Question 28
Refer to the exhibit.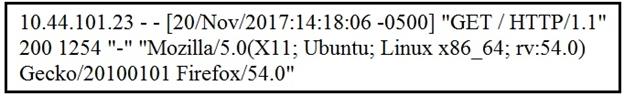
What does the message indicate?
Question 29
Refer to the exhibit.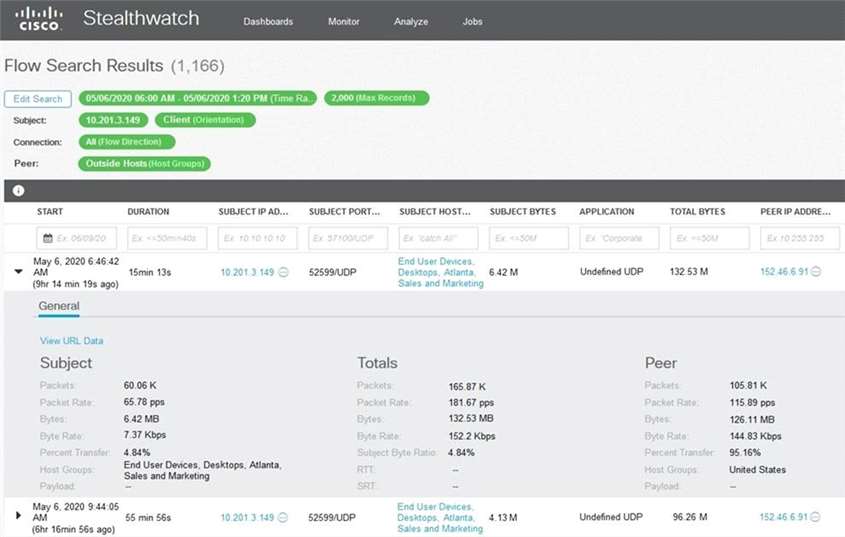
What is the potential threat identified in this Stealthwatch dashboard?
Question 30
A SOC analyst is investigating an incident that involves a Linux system that is identifying specific sessions.
Which identifier tracks an active program?