Question 46
How does an attacker observe network traffic exchanged between two users?
Question 47
Refer to the exhibit.
Which type of log is displayed?
Question 48
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
Question 49

Refer to the exhibit. In which Linux log file is this output found?
Question 50
Refer to the exhibit.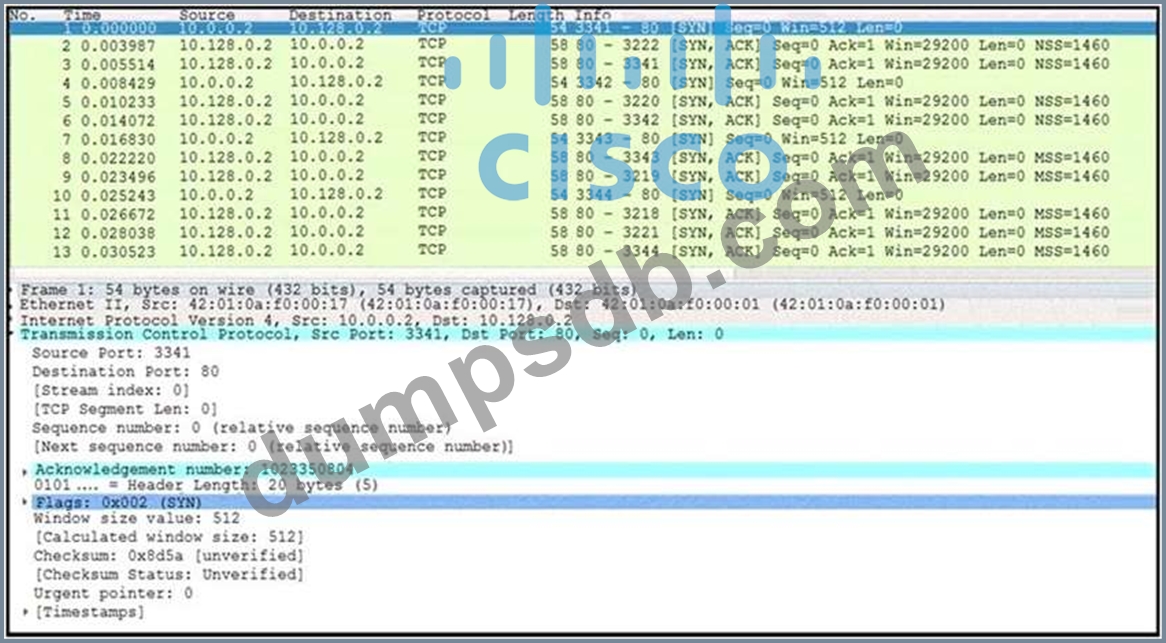
What is occurring in this network traffic?

