Question 66
What is an example of social engineering attacks?
Question 67
You have identified a malicious file in a sandbox analysis tool. Which piece of file information from the analysis is needed to search for additional downloads of this file by other hosts?
Question 68
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
Question 69
Refer to the exhibit.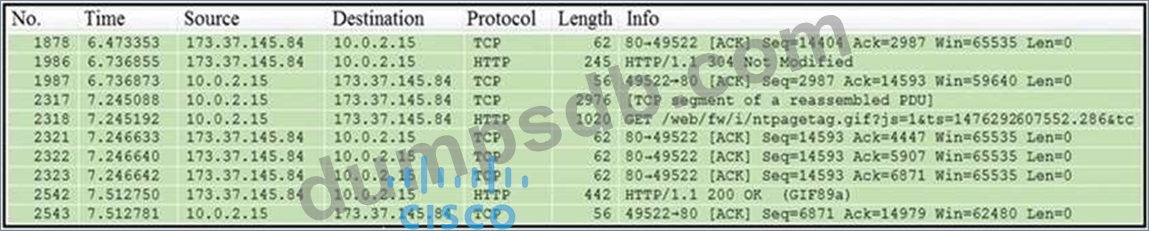
Which packet contains a file that is extractable within Wireshark?
Question 70
Which of these describes SOC metrics in relation to security incidents?

