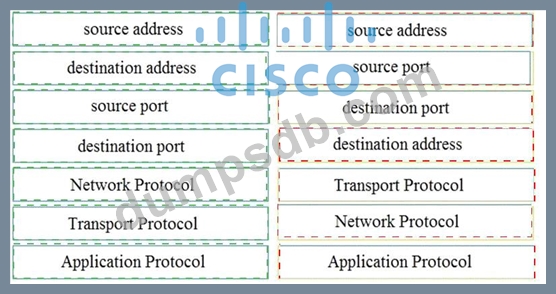
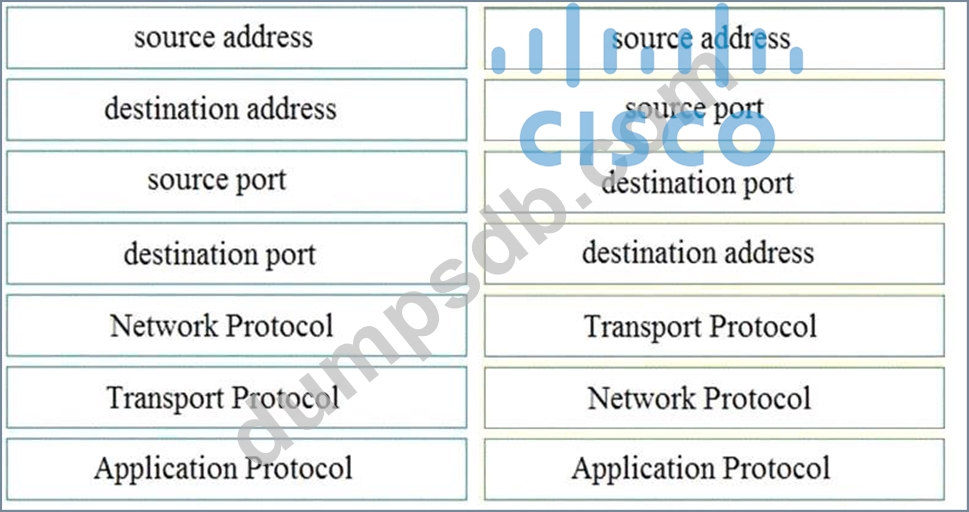
Question 76
Refer to the exhibit.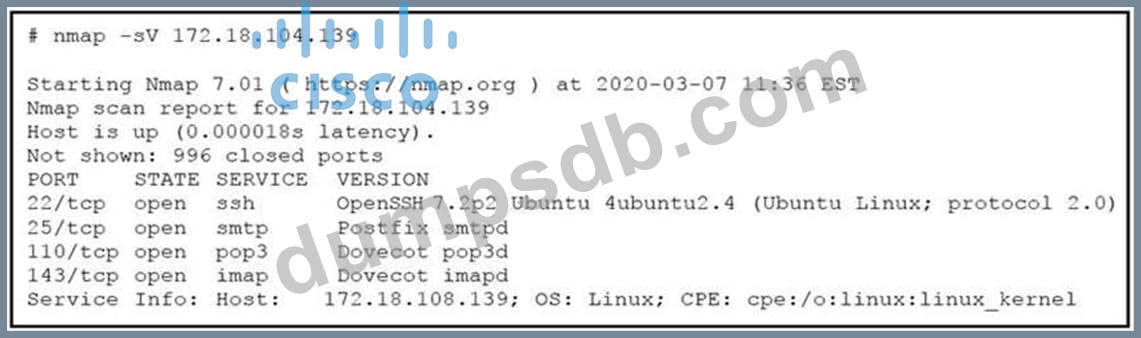
What does the output indicate about the server with the IP address 172.18.104.139?
Question 77
Which type of verification consists of using tools to compute the message digest of the original and copied data, then comparing the similarity of the digests?
Question 78
Refer to the exhibit.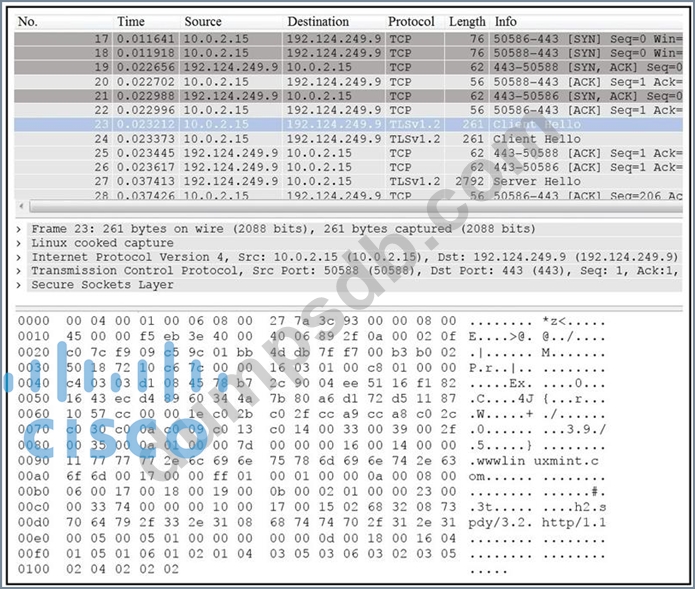
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.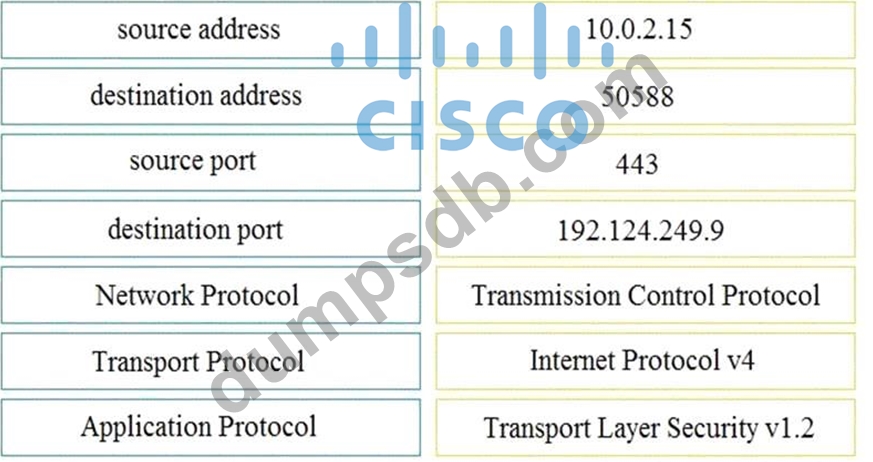
Question 79
A security incident occurred with the potential of impacting business services. Who performs the attack?
Question 80
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?