Question 86
Refer to the exhibit. What does this output indicate?
Question 87
Refer to the exhibit.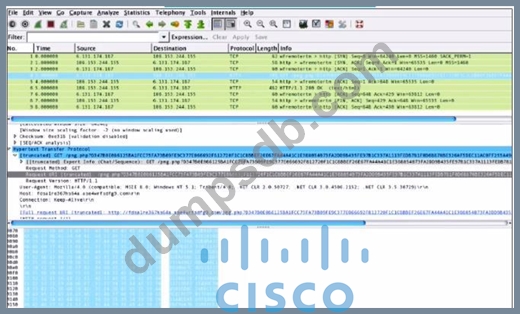
What is shown in this PCAP file?
Question 88
An offline audit log contains the source IP address of a session suspected to have exploited a vulnerability resulting in system compromise.
Which kind of evidence is this IP address?
Question 89
Which system monitors local system operation and local network access for violations of a security policy?
Question 90
Why is HTTPS traffic difficult to screen?

