Question 71
How is NetFlow different from traffic mirroring?
Question 72
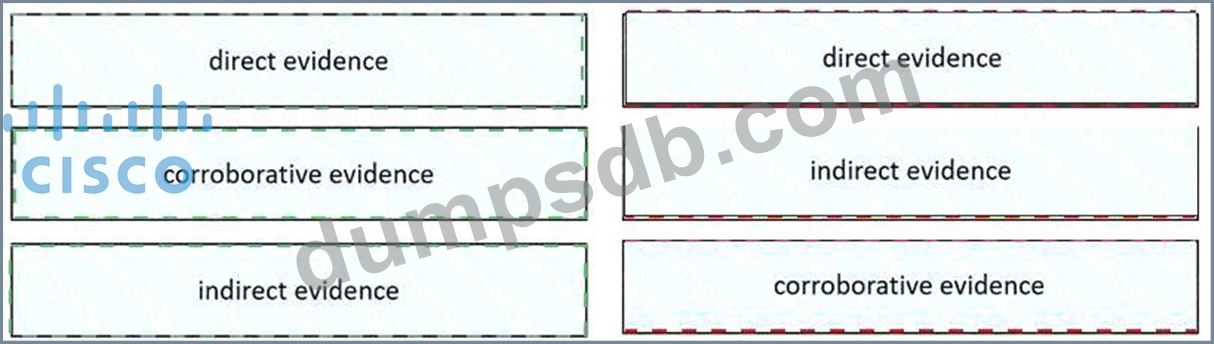
Drag and drop the type of evidence from the left onto the description of that evidence on the right.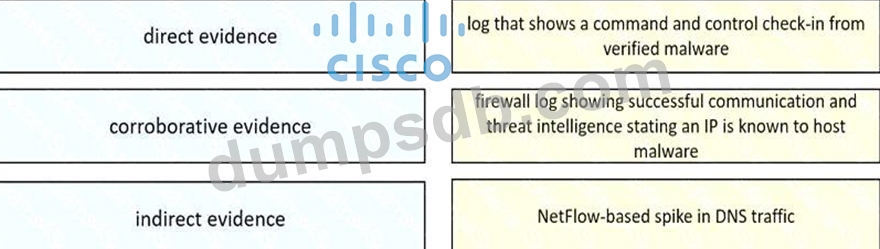
Question 73
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
Question 74
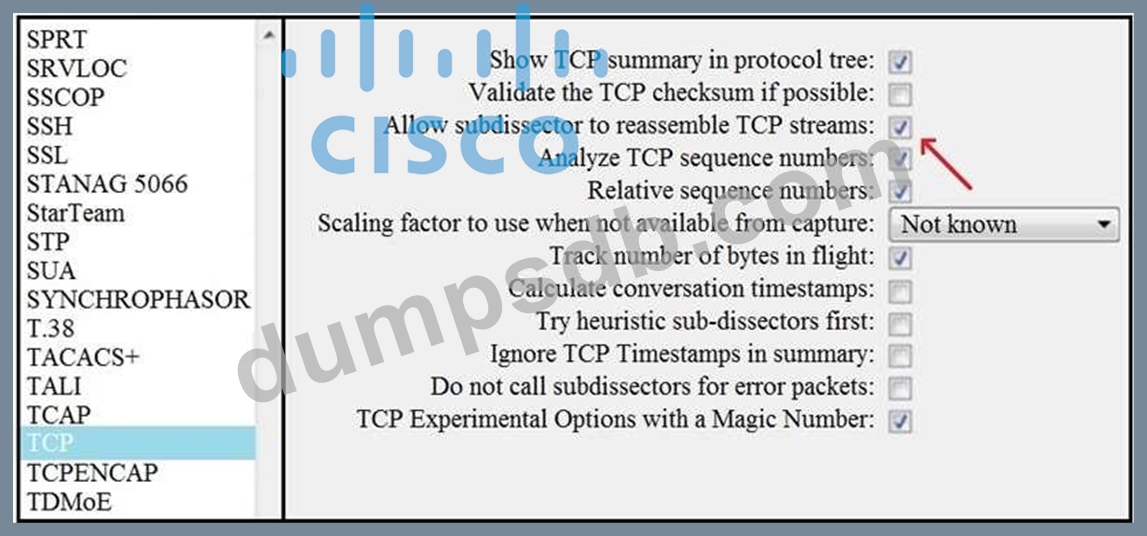
Refer to the exhibit. What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Question 75
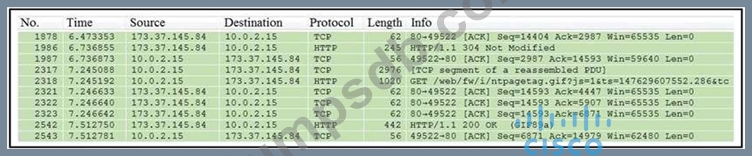
Refer to the exhibit. Which packet contains a file that is extractable within Wireshark?