Question 56
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
Question 57
How does an attack surface differ from an attack vector?
Question 58
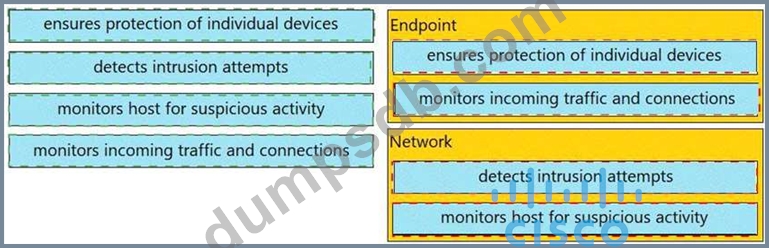
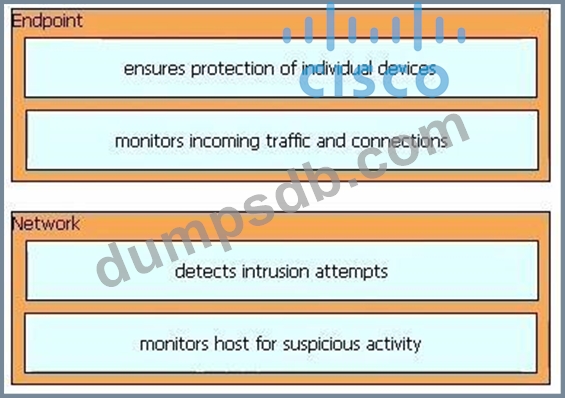
Drag and drop the uses on the left onto the type of security system on the right.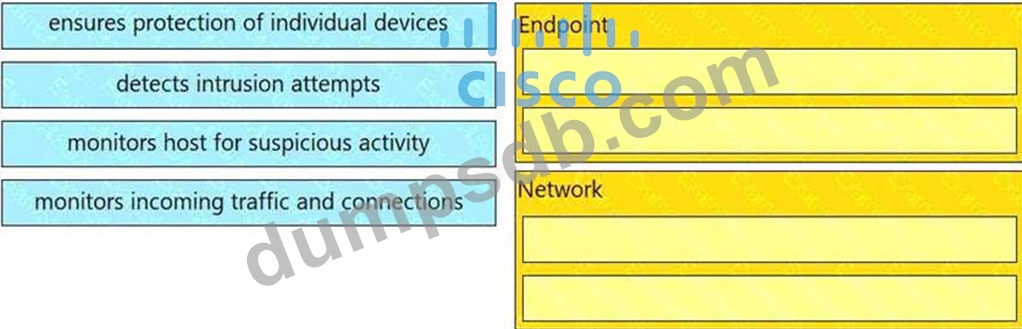
Question 59
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
Question 60

Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?