Question 61
An analyst discovers that a legitimate security alert has been dismissed.
Which signature caused this impact on network traffic?
Question 62
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
Question 63
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
Question 64
Which vulnerability type is used to read, write, or erase information from a database?
Question 65
Refer to the exhibit.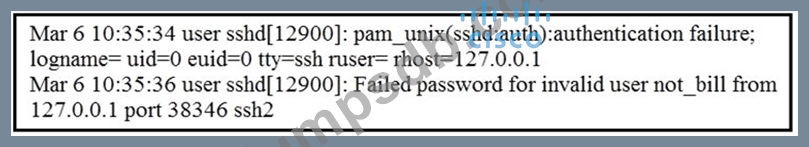
In which Linux log file is this output found?

