Question 81
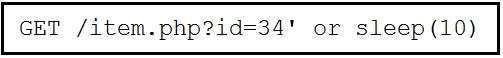
Refer to the exhibit. This request was sent to a web application server driven by a database.
Which type of web server attack is represented?
Question 82
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network.
What is the impact of this traffic?
Question 83
Refer to the exhibit.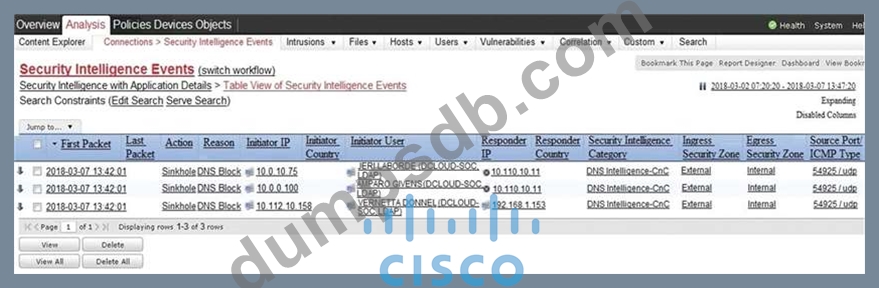
Which two elements in the table are parts of the 5-tuple? (Choose two.)
Question 84
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
Question 85
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?

