Question 101
A malicious file has been identified in a sandbox analysis tool.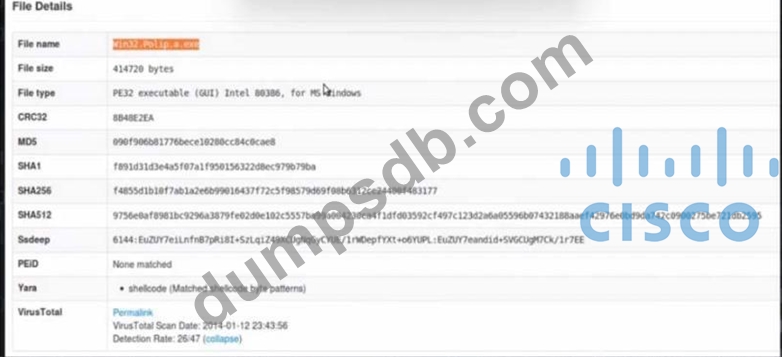
Which piece of information is needed to search for additional downloads of this file by other hosts?
Question 102
One of the objectives of information security is to protect the CIA of information and systems.
What does CIA mean in this context?
Question 103
Refer to the exhibit.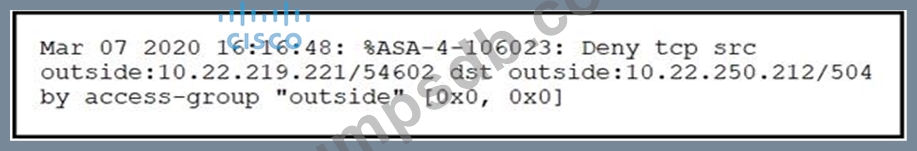
Which technology generates this log?
Question 104
What is the practice of giving an employee access to only the resources needed to accomplish their job?
Question 105
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?

