Question 91
What is the difference between the ACK flag and the RST flag?
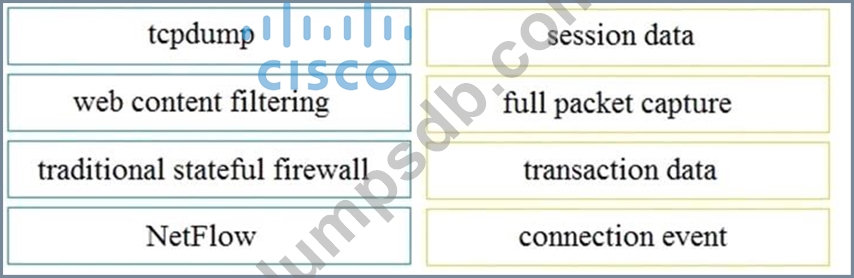
Question 92
Drag and drop the technology on the left onto the data type the technology provides on the right.
Question 93
What is the difference between vulnerability and risk?
Question 94
An intruder attempted malicious activity and exchanged emails with a user and received corporate information, including email distribution lists. The intruder asked the user to engage with a link in an email.
When the fink launched, it infected machines and the intruder was able to access the corporate network.
Which testing method did the intruder use?
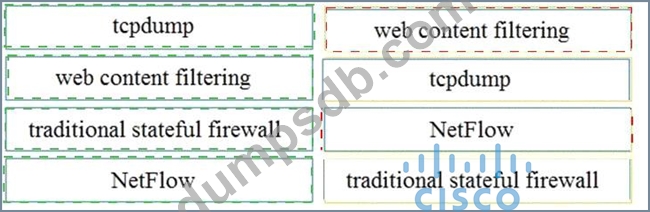
Question 95
Drag and drop the technology on the left onto the data type the technology provides on the right.