Question 86
An organization subscribes to multiple third-party security intelligence feeds. It receives a notification from one of these feeds indicating a zero-day malware attack is impacting the SQL server prior to SP 2. The notification also indicates that infected systems attempt to communicate to external IP addresses on port 2718 to download additional payload. After consulting with the organization's database administrator, it is determined that there are several SQL servers that are still on SP 1, and none of the SQL servers would normally communicate over port 2718. Which of the following is the BEST mitigation step to implement until the SQL servers can be upgraded to SP 2 with minimal impact to the network?
Question 87
A company that is hiring a penetration tester wants to exclude social engineering from the list of authorized activities. Which of the following documents should include these details?
Question 88
The Chief Executive Officer (CEO) instructed the new Chief Information Security Officer (CISO) to provide a list of enhancement to the company's cybersecurity operation. As a result, the CISO has identified the need to align security operations with industry best practices. Which of the following industry references is appropriate to accomplish this?
Question 89
A vulnerability analyst needs to identify all systems with unauthorized web servers on the 10.1.1.0/24
network. The analyst uses the following default Nmap scan:
nmap -sV -p 1-65535 10.1.1.0/24
Which of the following would be the result of running the above command?
Question 90
A newly discovered malware has a known behavior of connecting outbound to an external destination on port 27500 for the purposes of exfiltrating data. The following are four snippets taken from running netstat -anon separate Windows workstations: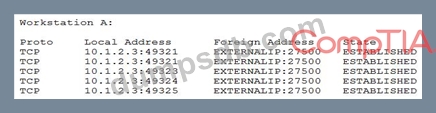



Based on the above information, which of the following is MOST likely to be exposed to this malware?

